A. Introduction to the Domain Name System (DNS):
Established in the last century, the Domain Name System (DNS) remains a critical part of the Internet [1]. The DNS acts as a registry on the global network. For example, it translates human-readable names such as “example.com” into IP addresses that computers use to identify each other on the network [2].
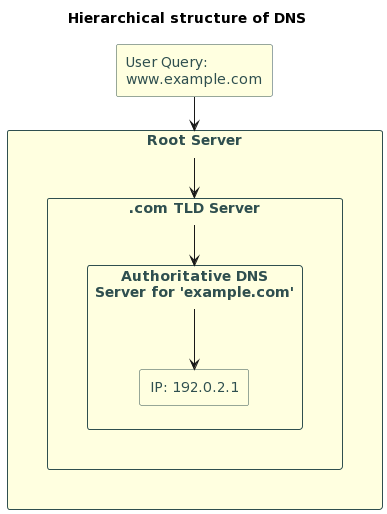
Diagram 1: A simple flowchart or infographic that demonstrates how DNS translates human-readable domain names to IP addresses.
DNS allows users to easily access websites without having to remember complex numerical IP addresses [3].
However, despite the apparent simplicity and reliability of DNS, its centralised and hierarchical structure has led to problems such as security vulnerabilities and administrative complexity [4].
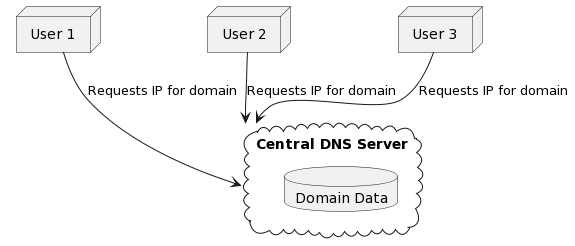
Diagram 2. Centralized Nature of DNS.
In addition, the main problem with DNS is the lack of ownership of domain names and the inadequate identification of their owners, which leads to a lot of abuse. Based on my own experience with the domain name market, having managed several domain name registrars for more than 12 years, being a co-owner of .SU and participating in the management of the state domain zones .RU and RF, I can responsibly state that up to 40% of domain names belong to a narrow circle of people who use them for various purposes, not necessarily illegal, but in most cases causing significant damage to the global network and users.
The exhaustion of convenient names in popular domain zones inevitably leads, and has already led, to the creation of additional first-level root zones, already numbering in the thousands, which certainly increases the entropy of the global Internet. With these initial data, we have come to the beginning of our work on this article.
B. Introduction to the IPvX ecosystem
The idea of the IPvX (Internet Protocol version X) ecosystem was initiated by the Private Institute for the Development of Public Digital Networks IEDN gGmbH and emerged in response to the aforementioned challenges and the growing demands of the digital age.
With the increasing use of decentralised systems based on blockchain technology, the internet infrastructure itself is in need of a major overhaul and paradigm shift. So far, any changes discussed in the community have focused more on refining existing Internet protocols and their interactions, as shown in this study [5]. But it is time to radically move away from the existing Internet governance mechanisms.
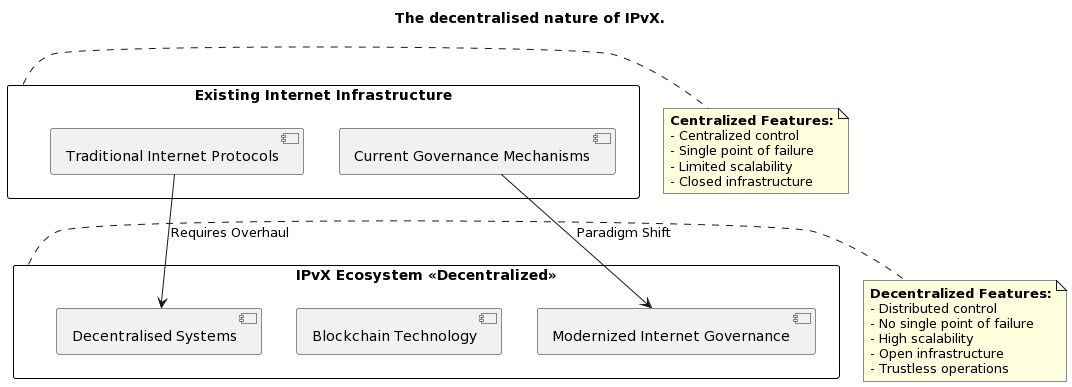
Diagram 3. The decentralised nature of IPvX.
The new IPvX protocol represents a decentralised approach to identifying and accessing network resources. At the heart of this transformation is the aggregated identification of network nodes in a single blockchain registry, the integration of Non-Fungible Token (NFT) technology, which provides unique, immutable and verifiable identifiers for each resource in the network [6]. And the use of smart contracts to describe and enforce rules for information transfer and identification of all participants in the process.
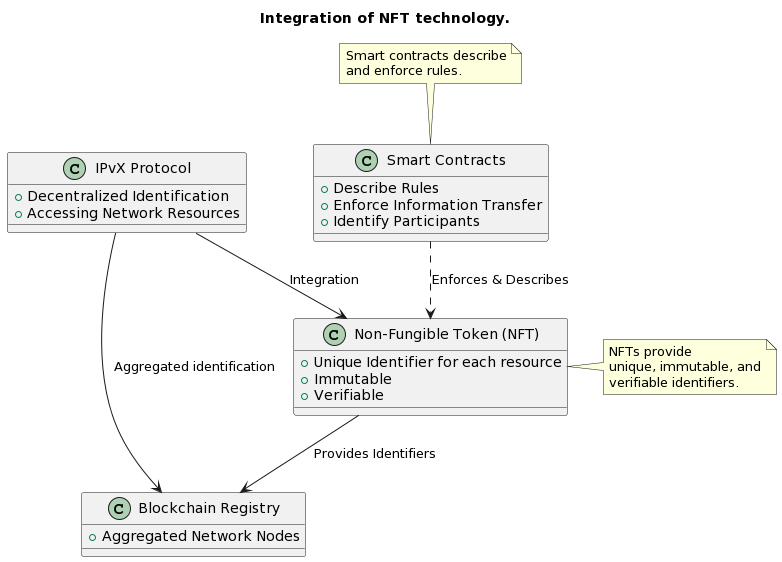
Diagram 4. Integration of NFT technology.
C. The purpose of the article
The purpose of this paper is to attempt to provide the expert community with an alternative view of the possible path of global network infrastructure development. Within the framework of this paper, we will consider the possibility of a transition from the traditional DNS system [2] to the use of NFT identifiers in the IPvX ecosystem [6].
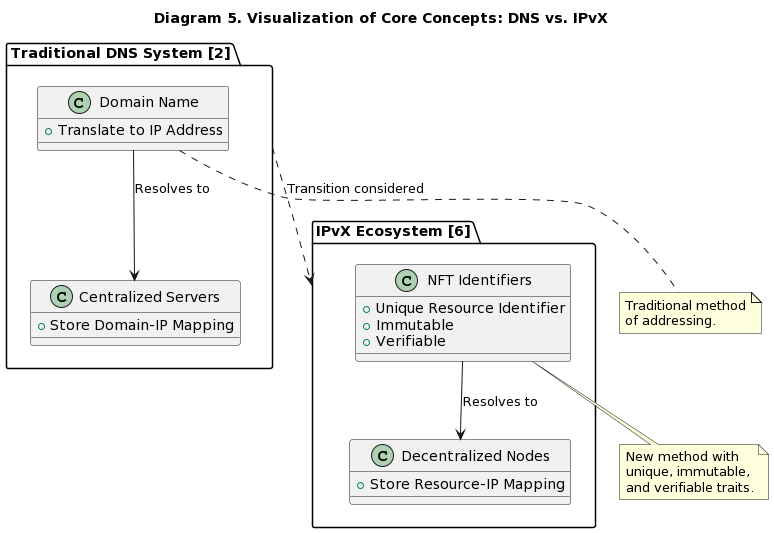
Diagram 5. Visualization of Core Concepts: DNS vs. IPvX
In this paper we will take a detailed look at how both systems work [3], compare their features and functionality [7], and explore the possible problems that await us in the future if this technology is implemented [8].
Whether you are a network expert, a digital rights advocate, or simply curious about the next stage of the Internet’s development, this study promises to look beyond the new digital frontier [9].
II. Background on IPvX and the Concept of NFT Identifiers
A. Introduction to IPvX: Implementing Blockchain in IP Addressing.
In recent years, it has become clear that the solutions used for the Internet infrastructure are seriously outdated and no longer meet the requirements of changing market relations or fundamentally new systems for managing production and business processes [9].
The widespread integration of a large number of networked devices requires not only new security measures, but also a clear and accessible navigation system for society [5]. The basis for this is address routing. While we anticipate objections from proponents of routing through the application layer, which is possible as a secondary distribution of information flows [2], we should remember that the root infrastructure should be built on the principle of
“Every wire has two ends, and there is something at each end”.
This means that we cannot fundamentally change the approach to routing from sender to receiver, but we can significantly change the architecture of this process, eliminating many of the existing shortcomings and fundamentally changing the principles of network and address resource management [22,25].
This is why we propose to use distributed ledger technology, or “blockchain”, as the basis for the network infrastructure[8,12].
Blockchain, with its decentralised nature and history of providing secure, transparent and immutable accounting, will enable a more streamlined, secure and adaptable method of Internet addressing [7][16].
Leveraging the distributed ledger capabilities of the blockchain, the IPvX system we are developing will ensure that every addressing transaction is transparent, verifiable and tamper-proof, creating a secure foundation for the future of the Internet [13].
B. Unique Addressing Structure in IPvX
To understand the nature of the changes that the new IPvX ecosystem being developed by IEDN [10] will bring to the network, it is necessary to visualise the structure of the new IPvX network address. The new IPvX address is a multi-dimensional entity that encompasses three main tasks required of it in today’s environment:
Address Format: Address Integration of Blockchain, NFT and Smart Contract Addresses
As mentioned above, the multi-component addressing structure of IPvX is an integration of three central components:
Blockchain Address: Serves as the basic component in IPvX and uniquely identifies a node or user. A typical address can be generated on the IPX blockchain, our customised solution that is
created by us specifically for this purpose [12]
{
“BlockchainAddress”: {
“Type”: “IPX Blockchain”,
“Value”: “IPX#0x23fB5A7aCa1234567ABcD8Ef9GHiJ5kLm0”
}
}
In general, well-known blockchains such as Ethereum [31] or Polkadot can also be used for rapid implementation, but the best solution is to develop your own blockchain specialised in internet infrastructure and related transactions [13].
NFT (Non-Fungible Token): NFT is not only a symbol of ownership in the system for each resource, but also provides a unique identification of those resources, whether it is a device or a service. This means that with the help of the NFT token or identifier, it is not only possible to determine the point of sending or receiving information by blockchain address, but also to ensure that this resource really belongs to a particular user and that they have the right to send and receive this information on their behalf [6]. Using the Ethereum ERC-721 or Flow blockchain framework, an NFT picture could look like this:
{
“NFT”: {
“Platform”: “Ethereum ERC-721”,
“Identifier”: “NFT#321-4567-890A-BCDE”
}
}
Smart Contracts: define the rules for the behaviour of all IPvX address related transactions, they include in their code rules and protocols that ensure consistent and reliable communication between network objects [7]. Platforms such as Ethereum [31] or Binance Smart Chain can provide a solid foundation to start implementing IPvX technology. But later on, of course, you will need your own system for generating and storing them.
An example of a smart contract record might be
{
“SmartContract”: {
“Platform”: “Ethereum”,
“Reference”: “SC#987-6543-210X-YZAB”
}
}
A complete IPvX address record might look something like this when all these components are combined:
{
“IPvXAddress”: “IPX#0x23fB5A7aCa1234567ABcD8Ef9GHiJ5kLm0:NFT#321-4567-890A-BCDE:SC#987-6543-210X-YZAB”
}
This recording format allows you to get the maximum effect from the synergy of several key components that, in fact, allow, as in the physical topology, to carry out digital triangulation to precisely determine the location of the node in the network and to see all its basic parameters [9].
Advantages over conventional addressing mechanisms.
The IPvX structure offers many advantages over traditional IP addressing:
High level of security [16].The cryptography built into the structure of the IPvX address components makes any illegal manipulation of the address space impossible, as each address is protected from unauthorised changes and potential hacking.
Transparency of transactions [8].
All changes or transactions are recorded on the blockchain, providing complete transparency and reliability.
Adapts to changes in the Internet environment [14].
The use of smart contracts in IPvX addresses allows IPvX addresses to be configured and adapted to specific conditions, eliminating the need for centralised intervention and management.
Unlimited address generation.
With blockchain at its core, IPvX allows unlimited address generation, bypassing the traditional problems of limited registry and under-utilisation due to blockchain allocation [13]. As a result, the notion of address scarcity becomes irrelevant, ensuring that pre-generated addresses are always available to meet demand at any scale.
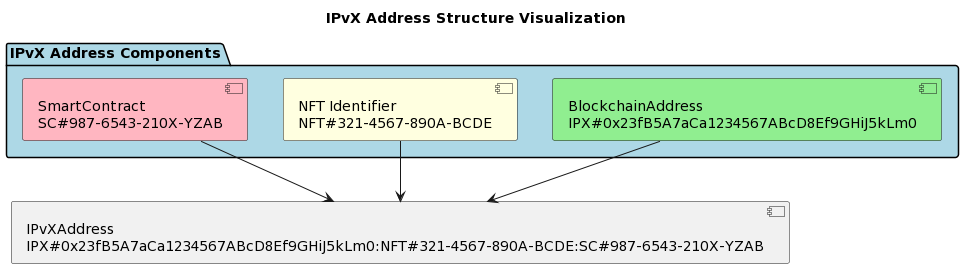
Diagram 6. IPvX Address Structure Visualization
In this way, the new type of network addressing allows for the creation of an infrastructure that adapts to the rapidly changing e-landscape of the Internet, independent of the human factor and the centralised mechanisms of Internet bureaucracy [10].
C. The structure of IPvX data packets.
The main parts of an IPvX packet: Headers, Payloads and Trailers.
In general, IPvX continues to build on the strengths of the traditional packet layout in the IP concept, specifically adding NFT identifiers and references to smart contracts, and using three-part blockchain-based addresses.
Headers: Version Field: Pinpoints the IPvX version.
Source and Destination Addresses: These are dynamic in size and are structured to include the blockchain IPX address followed by NFT-based identifiers and smart contract references.
Timestamp: Denotes the exact moment the packet was dispatched.
Time To Live (TTL): Illustrates the packet’s remaining lifespan within the network.
Protocol Field: Signifies the protocol overseeing the payload.
Header Checksum: A safeguard ensuring error detection during transmission.
NFT Packet Identifier: A singular identifier cementing traceability and packet distinction.
Smart Contract Packet Reference: Paves the way for dynamic network operations by linking directly to a specific smart contract for packet transmission.
Payload Length: Describes the extent of the packet’s content.
Options: Provides supplementary data or fields if necessary.
Padding: Ensures the header adheres to a standardized length.
Payload: a key component of a packet that carries basic data, such as messages, documents or even instructions.
Trailers: This segment may encapsulate elements like checksums, underscoring the packet’s authenticity while also signaling its conclusion.
Diagram 7. IPvX Data Packet Structure.
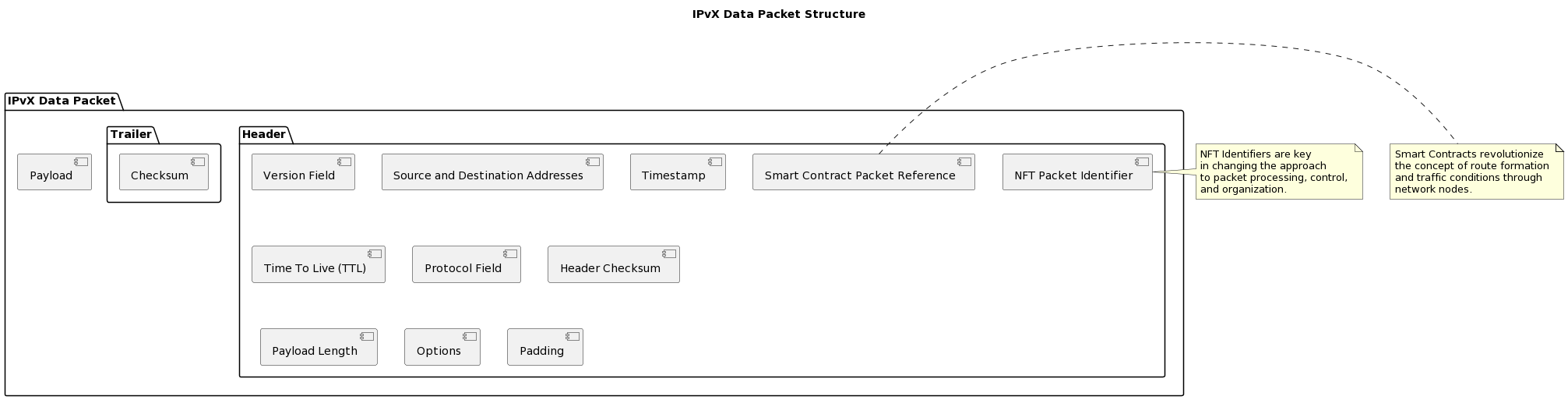
IPvX Data Packet Example:
{
“Header”: {
“Version”: “IPvX v1.0”,
“SourceAddress”: “IPX#1A2B3C4D:NFT-1234A789:SC-A1B2C3D4”,
“DestinationAddress”: “IPX#9Z8Y7X6W:NFT-9876Z543:SC-Z9Y8X7W6”,
“Timestamp”: “2023-08-07 12:34:56 UTC”,
“TTL”: 128,
“Protocol”: “TCP”,
“Checksum”: “AF38”,
“NFTPacketIdentifier”: “NFT-1234A789”,
“SmartContractReference”: “SC-A1B2C3D4”,
“PayloadLength”: 512,
“Options”: “None”,
“Padding”: 16
},
“Payload”: “Hello, this is a sample message sent via IPvX from one device to another. This message is being routed and processed using the cutting-edge features of the IPvX protocol, including blockchain IPX addressing, NFT-based identification, and smart contract references.”,
“Trailer”: {
“Checksum”: “D7E2”
}
}—
As a result, the IPvX packet becomes a new means of information delivery with enormous potential through the use of adaptive customisation mechanisms contained in components such as smart contracts and NFT identifiers.
Significance of NFT Identifiers and Smart Contacts in Packet Formation and Delivery
Importance of NFT and Smart Contract Identifiers in Packet Generation and Delivery.
The integration of NFT identifiers directly into the IPvX header leads to a change in the approach to the process, detection and identification of data packets, their control and organisation.
By using NFT-based addresses in combination with blockchain-based IPX addressing, each packet becomes unique and therefore easily traceable.
In addition, the presence of an NFT identifier provides a tamper-proof method of identifying packets, facilitating the use of decentralised routing.
The use of smart contracts in the formation and delivery of packets in the IPvX network fundamentally changes the concept of route formation and the conditions under which traffic passes through network nodes.
Here are the main features that can be provided by smart contracts written into the data transmission packet.
Route conditions – When creating a route in the blockchain network based on the current state, at the request of the sender node (the procedure we will consider in the next section), this route is placed in a self-executing smart contract and added to the data packet in a place with an NFT identifier that makes this packet unique.
Dynamic rerouting – If there are problems sending a packet, or if the route is not optimal, or if the node specified in the route does not respond, the smart contract can contain information about alternative routes and reroute the packet along an alternative, optimal route.
Access control – Smart contracts can verify and authenticate the source and destination of packets, ensuring that data is only sent and received by authenticated entities, greatly reducing malicious activity on the network.
Privacy and data protection – Smart contracts can facilitate data encryption, ensuring that packets are only available to the intended recipient. They can also enforce data processing and storage protocols to ensure compliance with privacy regulations.
While traditional networks have relied on static configurations, manual intervention and trust relationships, the integration of smart contracts can automate and optimise packet formation and delivery, bringing a higher level of transparency and trust.
D. Technical overview of data transport in IPvX networks: An Engineering Perspective on Node Interaction
To understand the mechanism of action of the protocol we are designing, we can consider a model of the sequence of operations that occur when a node connects to the network and sends a request to another node [22][25].
Sequential stages of data transmission:
1. Request generation:
A device (or end-user node) initialises a communication task, be it receiving web content or sending an email [9]. This device communicates with its primary node, technically known as the initiator [9].
2. Requesting a network address: Upon recognising a request, the initiator checks whether the sender has a previously assigned address [2][18]. If not, it contacts a decentralised address repository controlled by a consortium of miners or validators [6][16].
This repository stores algorithmically generated blockchain addresses, eliminating the need for a centralised address assignment module [12][14]. The initiator also contacts the miners/validators to obtain an NFT token and smart contract to complete the address, as these are individualised and cannot be created and placed in the pool in advance [6][7].
If the sender already has an assigned address, the existing address will be used [2][18].
3. Route calculation:
Upon receiving a new address or verifying that an existing address exists, the initiator contacts the miner/validator nodes to request a route [25].The miners/validators in turn contact the blockchain repository, which provides a dynamic view of the operational state of the network [13].
This information is used to compute an efficient data path, with particular attention paid to minimising obstacles in the path and ensuring that the path is short [25]. The path information is encoded in a smart contract, which is sent to the initiator and placed in a data packet [7].
4. Blockchain integration
Once the path has been calculated and added to the smart contract, the miners/validators encapsulate it into a block and add it to the blockchain vault [12][13]. This serves as an immutable record, providing transparency and traceability of each route determination [12][14].
5. Data propagation:
A data packet begins its journey by passing through intermediate nodes, similar to routers in legacy systems [9]. These nodes store the details of the intended path, confirming the packet’s progress [9][22]
6. Delivery to Destination: The packet completes its journey at the destination node where it is decoded and delivered. 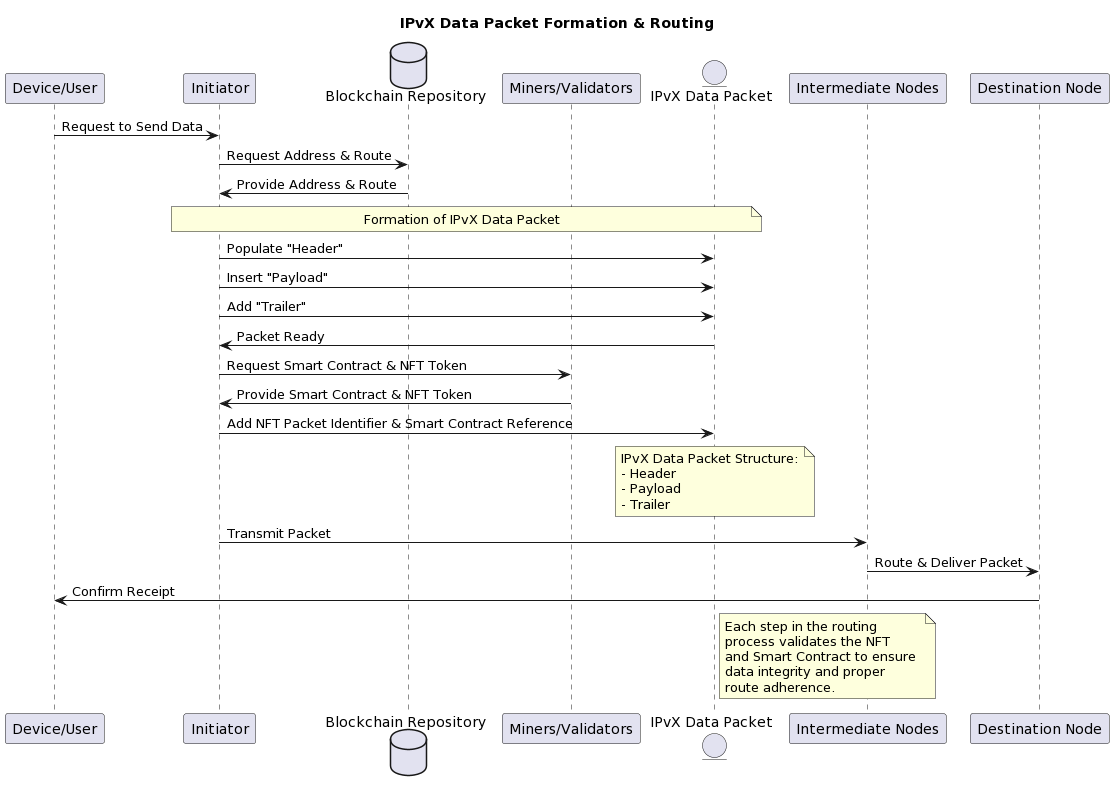
Diagram 8. IPvX Data Packet Formation & Routing.
Communication mechanism between nodes:
Let’s look at the main nodes of the IPvX network:
Initiator: after receiving a request from the sender, initiates the data exchange process, checks the availability of an address and, depending on its availability, requests the address first [9][22].
Miners/Validators: perform several functions
Blockchain storage
Intermediate node: Acts as a communication channel, confirming that a packet has travelled along a given path and reached its destination [9][22].
End node
The final receiver that decodes and interprets the data [9][22]
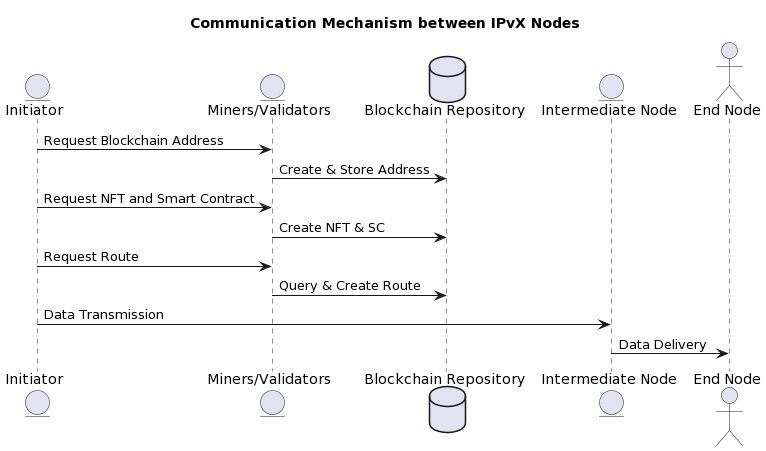
Diagram 9. Communication Mechanism between IPvX Nodes.
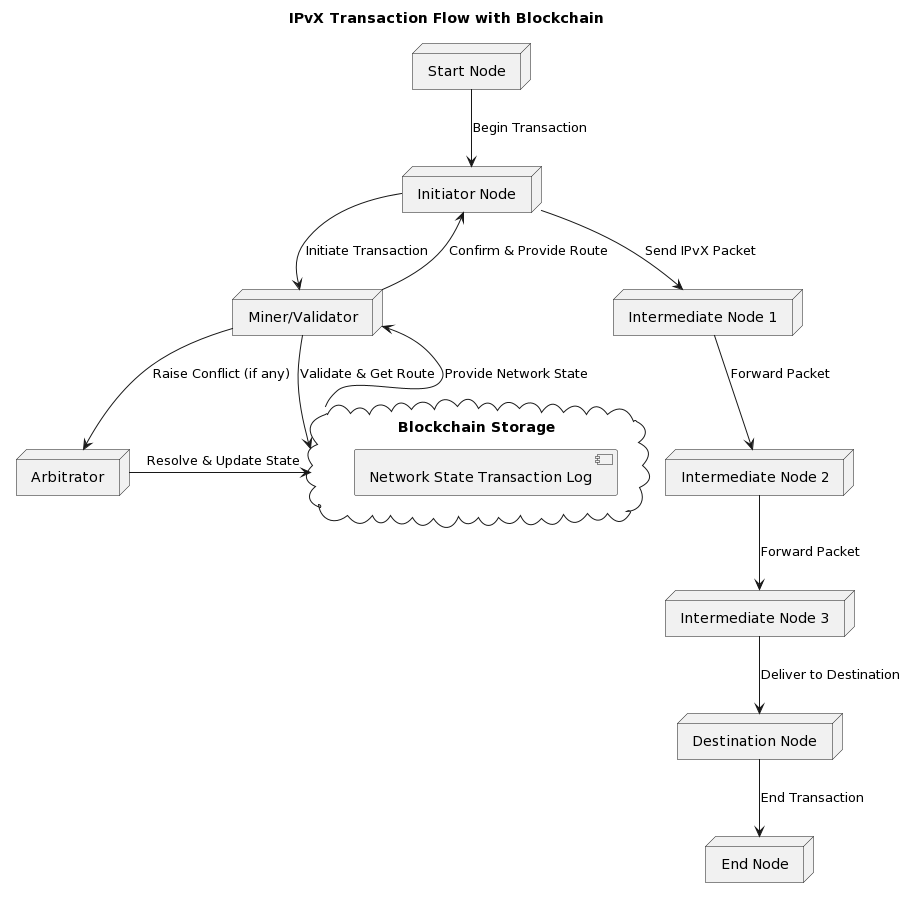
Diagram 10. IPvX Transaction Flow with Blockchain.
Arbitration mechanism in data transmission:
The arbitration module is responsible for resolving any disagreements in data transmission [9]. This layer resolves any contention resulting from simultaneous data requests, packet collisions or traffic congestion [9][25]. The system uses algorithmic determinants that weigh factors such as priority, queue length and transmission history to arbitrate and provide the optimal transmission path, ensuring smooth network operation.
The interaction of IPvX network nodes thus provides a high degree of decentralised communication for data transmission [25].
IPvX Network Process Flow
Let’s look at the process flow of the sequence of operations in the IPvX address allocation and routing process.
1. Request from user/initiator**: The user or initiator sends a request to obtain an IPvX address or to transmit data.
2. Address availability check**: The system checks whether the user has an existing IPvX address.
– If there is no address:
a. The initiator accesses the blockchain repository.
b. The initiator obtains a blockchain address from a decentralised address pool.
c. The miner associates an NFT and a smart contract with the blockchain address.
d. The IPvX address obtained is returned to the user and the initiator.
– If the address already exists:
a. The process continues with a route request from the initiator (step 3).
3. Route request from the initiator: the initiator requests a route from the miner.
4. Access to blockchain repository: The miner accesses the blockchain repository to get an up-to-date snapshot of the network.
5. Route creation: The miner creates and returns a route in the form of a smart contract.
6. NFT token creation: The miner creates an NFT token for the route.
7. Send smart contract and NFT token: The smart contract and NFT token are sent to the initiator and included in the data packet.
8. Returning the executed smart contract: The initiator sends the executed smart contract back to the miner.
9. Add the route to the blockchain: After verification, the miner adds the executed route to the blockchain as a new block.
10. Data transfer: The data transfer process begins. 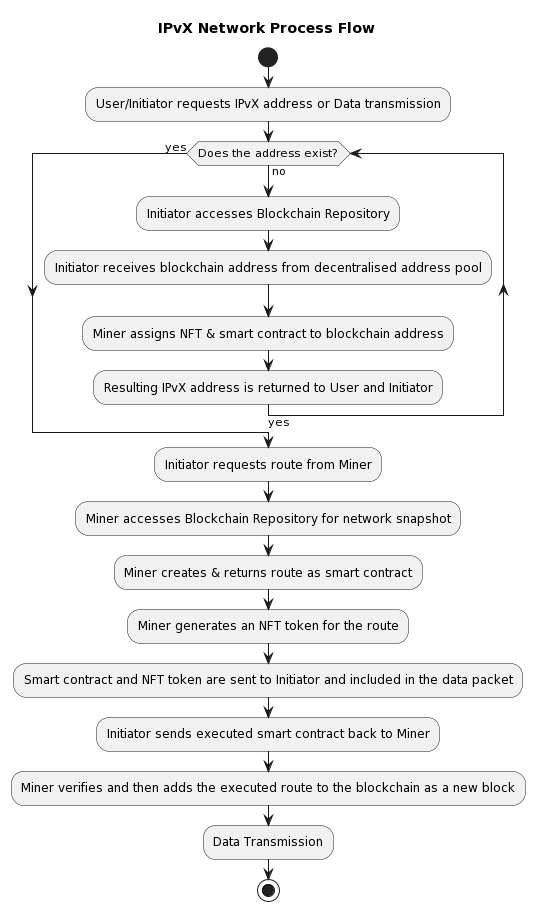
Diagram 11. IPvX Network Process flow. View 1.
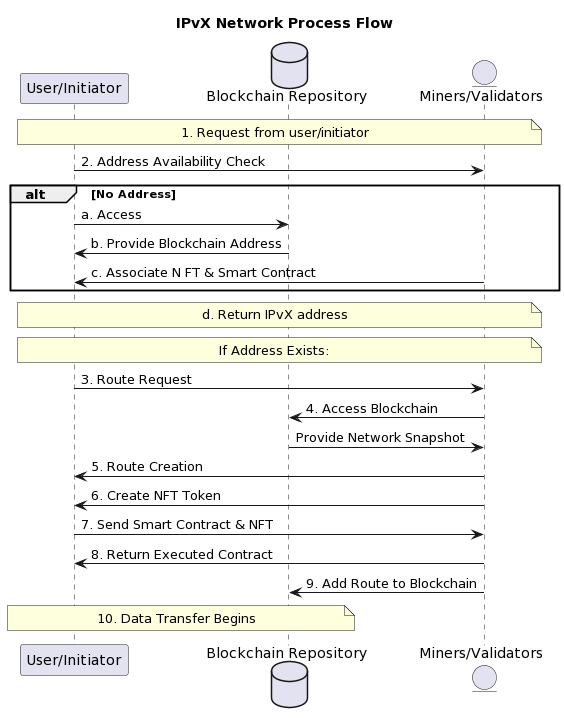
Diagram 12. IPvX Network Process flow. View 2.
E. Functional specification of miners and validators in an IPvX network.
Miners/validators are a key component of an IPvX network and are responsible for core functionality. Such as generating addresses, formulating routes and interacting with the blockchain [1][2].
Functions of miners
1. Generate a cryptographically secure blockchain address.
Miners provide IPvX address credentials using cryptographic algorithms [3]. Each address contains blockchain address components, specific NFT tokens [6] and associated smart contracts [7].
2. Accumulate into a decentralised address pool.
The generated blockchain addresses are sent to a decentralised address pool that resides in a blockchain repository [8], ensuring that addresses are immediately available to meet the connectivity needs of new devices [9].
Once the initiator selects a new blockchain address, the miner creates and adds specific NFT tokens and smart contracts to it [6][7]. The resulting address is transmitted to the initiator and simultaneously added to the issued address pool.
3. Route creation.
When formulating optimal paths for routing data packets, miners interact with the blockchain repository to access the most up-to-date state of the network.
This real-time interaction allows miners to create cryptographically verifiable paths that ensure efficient and secure data transmission across the network [11].
4. Add a route to the blockchain.
After completing a route, miners convert this information into a new block [12]. After verification, this block is added to the blockchain. The inclusion of these routes as immutable records confirms their resistance to unauthorised changes and ensures their availability for future use [13][14].
Validation capabilities:
Transaction Validation and Blockchain Integration:
1. Transaction analysis.
Validators scrutinise all transactions related to the network [15]. Every action, whether it is the allocation of an IPvX address or the transmission of data packets, is rigorously checked against established IPvX protocol metrics [6].
2. consensus-based authentication.
Central to the IPvX validation principle is the consensus mechanism [17]. Validators, without a central governing body, collectively authenticate a transaction. Their collective validation ensures that only transactions that meet the established criteria are added to the blockchain [18].
3. Network ledger synchronisation.
Once validated, transactions are propagated through the network, ensuring that all nodes have a synchronised and up-to-date record of all network transactions [19].
In general, miners/validators create a unified mechanism of interaction between users and all elements of the blockchain, ensuring the operation of the entire decentralised IPvX system [20].
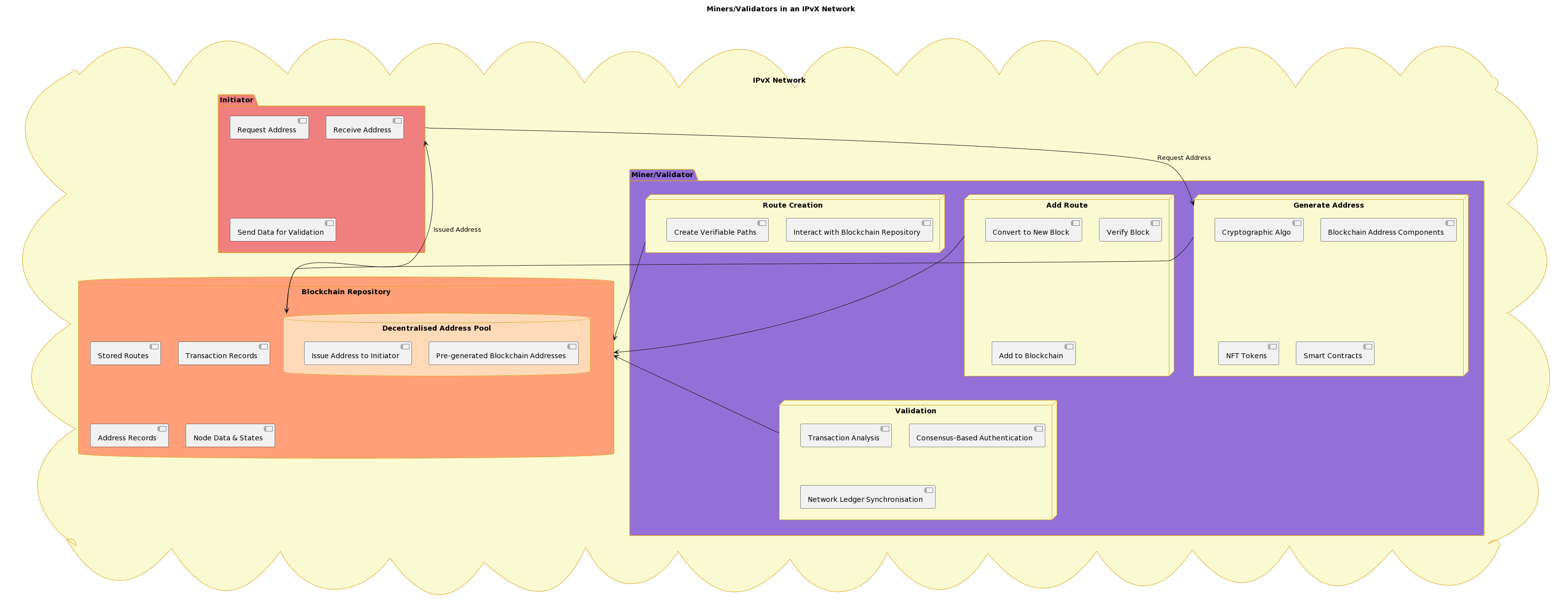
Diagram 13. Miners/Validators in an IPvX Network.
F. Protocol for enabling devices on an IPvX network: Technical Summary.
The integration of devices into an IPvX network, a blockchain-based digital communication system, requires a methodical approach based on engineering principles [1]. This document provides a systematic overview of the protocol used for device integration.
Initiator Node Communication Protocol:
When a device wants to integrate into an IPvX network, it starts by sending an initiation request to an initiator node [9].
After receiving the initiation request, the initiator node performs a programmed query to a centralised blockchain address repository. This repository contains a list of addresses that have been pre-computed by designated miners using cryptographic algorithms [12][13].
Address allocation mechanism.
Upon receiving a request from the initiator node,
the address repository, operating according to deterministic algorithms, selects an address for the requesting device [14].
The selected address serves as an identifier that defines the identity of each device on the network. This design ensures that no two devices have identical addresses, thus avoiding address collision scenarios [2].
Allocate , NFT tokens and smart contracts and generate an IPvX address.
After obtaining a blockchain address, it is necessary to allocate an NFT token in addition to it and form a smart contract [6][7].
Allocate the NFT token and deploy the smart contract.
After receiving information from the initiator node that it has received a blockchain address for the requested device, the miner can start forming an IPvX address. The associated NFT (Non-Fungible Token) is assigned to the device. Specifically, this token is of the ERC-721 type, known for its unique identification properties and adaptability to represent individual assets or organisations [6]. The ERC-721 token contains metadata attributes, ownership and other device-specific parameters, reinforcing its unique position in the network.
At the same time, a smart contract specifically designed for the operating parameters of the device is added [7]. This contract defines the operating conditions, permitted actions and any restrictions that the device must comply with on an IPvX network.
The result is a new IPvX address that is assigned to the device and is completely device-specific. This address is also added to the blockchain as a new block and made available to the entire network [8].
The integration of a device into an IPvX network is therefore a rigorous process governed by deterministic algorithms and engineering principles [1]. The protocol ensures that each device is not only integrated into the network, but also governed by explicit operating conditions, thus maintaining the integrity and functionality of the network [9].
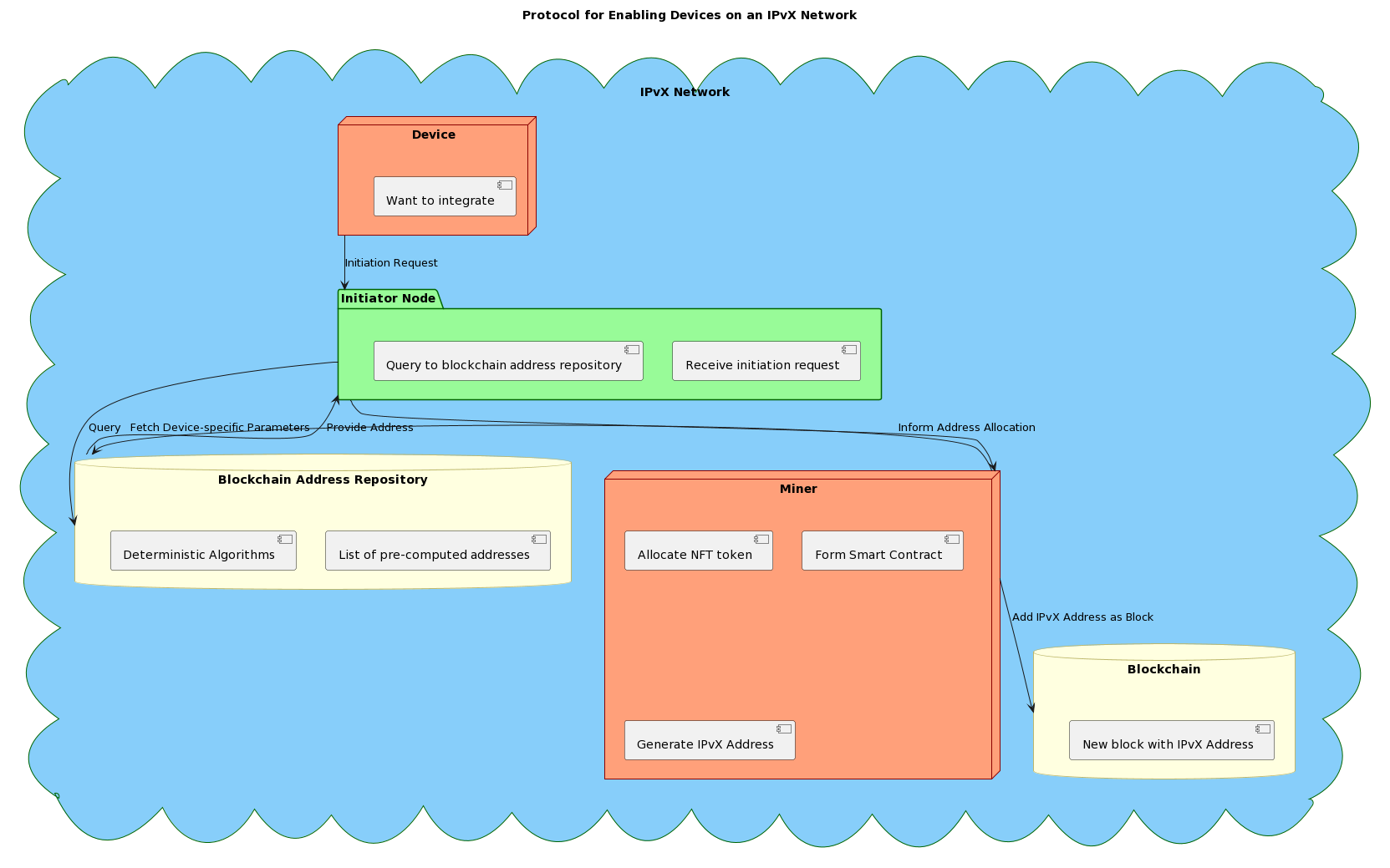
Diagram 14 . Protocol for Enabling Devices on an IPvX Network.
G. Defining routes for data transmission in the IPvX network structure.
The IPvX architecture integrates the mechanisms of blockchain technology for route discovery, which plays a central role in the process of orderly transmission of data over the network [12].
Obtaining network state data from blockchain storage.
Unlike traditional routing tables or similar constructs used to represent network topology, in an IPvX network this task is performed by a blockchain repository [12]. This decentralised repository is a registry of all states that is constantly updated with network transactions, topological changes and routing history [16].
Miners accessing this blockchain store provide a real-time snapshot of the network state, ensuring that the most up-to-date information is used to determine routes [17].
Optimal route formulation by failing miners.
– Upon receiving a data transfer request, vault miners initiate a consultation process with the blockchain store, extracting the necessary information to determine the most viable routes [31].
– Using heuristic algorithms and cryptographic principles, miner validators determine the optimal route for data packets [7]. Various metrics are taken into account, including latency, bandwidth availability and route security [5].
– Once determined, the route is encapsulated in a smart contract and offered for validation [7]. Upon successful validation, the route is added to the data packet and, once completed, it is also added to the blockchain as a verified block [14].
By basing routing decisions on real-time blockchain data, miners create optimal routes to ensure fast and secure data transfer, meeting the ever-increasing demands of modern communications [16].
H. The role of arbitrators in the IPvX ecosystem.
It is worth mentioning the arbitration procedures for various scenarios that may arise in the interaction of all participants in the IPvX system [16].
Arbitrators can resolve address ownership and routing disputes [11].
IPvX, which combines blockchain addresses, NFT tokens and smart contracts, offers a new addressing model [6]. However, it can sometimes lead to ambiguity in address ownership or allocation rights on the part of participants, either intentionally or unintentionally [16].
In such cases, arbitrators step in to determine the rightful owner based on transaction history, smart contract terms and time-stamped actions [7].
Routing disputes, on the other hand, can arise from disagreements over optimal paths or potential data leakage [5]. Arbitrators evaluate these disputes based on network logs, consensus agreements and blockchain records to ensure a fair resolution. [12]
Arbitration is a necessary part of any decentralised model, as even in a perfect system, disputes can arise and their resolution requires professional input from expert communities [8]. In the next section, we will talk about how this can be organised.
I. Moving from “Local Internet Registrars” to “Network Coordinators (NCs)”.
The new IPvX vision is to revise the function of ICANN and IANA and move away from centralised registry systems such as Regional Internet Registries (RIRs) and National Internet Registries (NIRs) [3]. These structures, which are responsible for resource allocation and billing in the modern Internet, are characterised by hierarchy and centralised control [9]. This leaves open the possibility of voluntary management decisions and, in the short term, the possibility of fragmenting the global Internet network and dividing it among regional players to serve domestic political interests.
From the centralised structure, however, it is possible to take structural units such as Local Internet Registrars (LIR) and transform them into a decentralised structure of Network Coordinators (NC), which can go into the format of a Decentralised Autonomous Organisation (DAO) [7].
Decentralised Autonomous Organisation (DAO), which inherently lacks centralised control.
Let’s look at the basic principles of Network Coordinators in the IPvX ecosystem
Core Node Support: NCs can technically support the operation of core nodes such as miners/validators, distributed blockchain storage and arbitrators.
Route and address allocation: In addition to technical and organisational support for core nodes, NCs with distributed computing power can dynamically route routes within the network and optimise decentralised address allocation by interacting with the blockchain storage to determine the most efficient routes and allocations in real time.
Network health monitoring.
In the DAO space, where centralised oversight is lacking, NCs can continuously monitor the health of the network and address potential bottlenecks, security vulnerabilities and system inefficiencies, ensuring that the network remains robust and flexible.
Facilitate arbitration.
Disputes are inevitable in a decentralised system. NCs will be able to play an important role in providing a link between aggrieved parties and arbitration mechanisms, ensuring that conflicts, whether related to address rights or routing, are resolved in a transparent and fair manner.
The IPvX Ecosystem as a Decentralised Autonomous Organisation (DAO) [7].
In general, the management of the new network architecture can be entrusted to a DAO, which is independent of any particular jurisdiction.
By its very nature, a DAO operates without a centralised authority. This structure prevents a particular network coordinator from exercising overarching control over an entire network or a group of other coordinators. Instead, he or she acts in concert with other coordinators to support the collective decision-making process.
Such interaction inevitably
increases the resilience and security of the network. By eliminating single points of failure and sharing responsibility, the system becomes more resilient to potential threats and vulnerabilities.
Overall, the potential of moving to a DAO model and integrating NCs promotes a democratic approach to truly managing the network. Decision-making is not limited to a central authority; instead, the wider community, through the network coordinators, plays an important role in shaping the trajectory of the network.
Monetisation options
It should also be noted that the use of DAO mechanisms paves the way for a new model of monetisation of the data transmission market. In this model, network participants will be able to offer their computing power in exchange for obtaining network addresses, transferring data or acquiring the necessary resources using an internal cryptocurrency such as an IPX token. Any member of the network can participate in the mining of addresses and routes and thus pay for their use. This system provides an alternative to the traditional model. In fact, in this configuration, network coordinators can replace traditional Internet service providers, leaving them only as infrastructure providers responsible for physical connectivity.
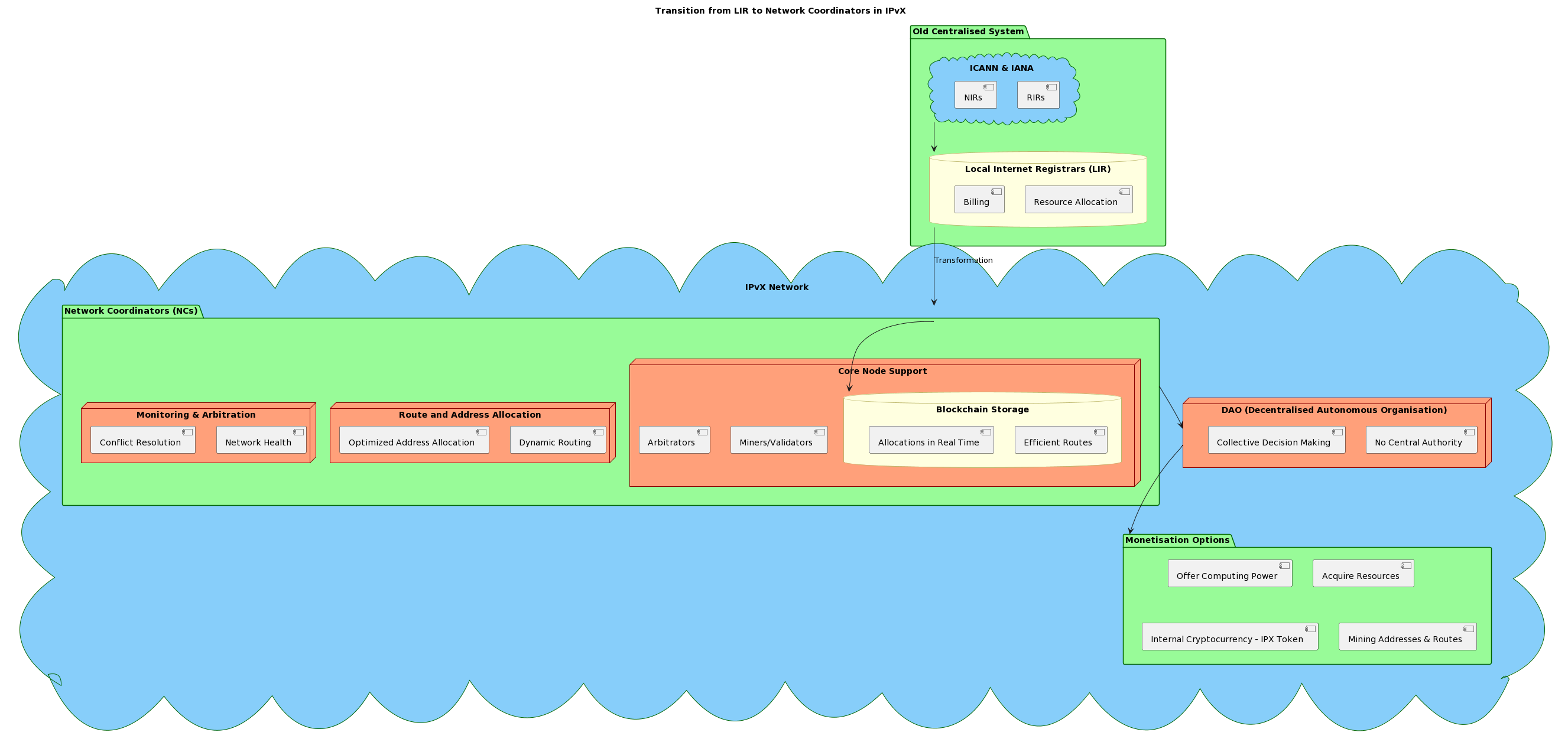
Diagram 15. Transition from LIR to Network Coordinations in IPvX.
J. Examples of addressing for different devices and nodes on an IPvX network
Example of allocating an IPvX address for a Coffee Machine:SmartCoffeeMaker
Device: SmartCoffeeMaker
1. Blockchain Address:
This address defines the primary identity of the coffee machine on the IPX blockchain. It’s akin to a physical address in the real world. By querying this address, you can fetch all the primary metadata about the coffee machine.
{
IPX:0xabcdef1234567890abcdef1234567890abcdef12
}
2. NFT Identifier:
Represents a unique digital identity or certificate for the coffee machine. This ensures the device’s unique representation in the blockchain network.
{
NFT:#765432109876
}
3. Smart Contract:
The smart contract governs the functionality, behavior, and rules associated with accessing and interacting with the coffee machine.
{
SC:0x1234abcd5678efgh1234abcd5678efgh1234ab
}
4. Alias or Short Name:
To simplify user access, an alias or short name is used. It’s a user-friendly identifier.
Based on the above, the full IPvX address for the “SmartCoffeeMaker” coffee machine might look like this:
{
IPX:0xabcdef1234567890abcdef1234567890abcdef12NFT:#765432109876/SC:0x1234abcd5678efgh1234abcd5678efgh1234ab/SmartCoffeemaker123
}
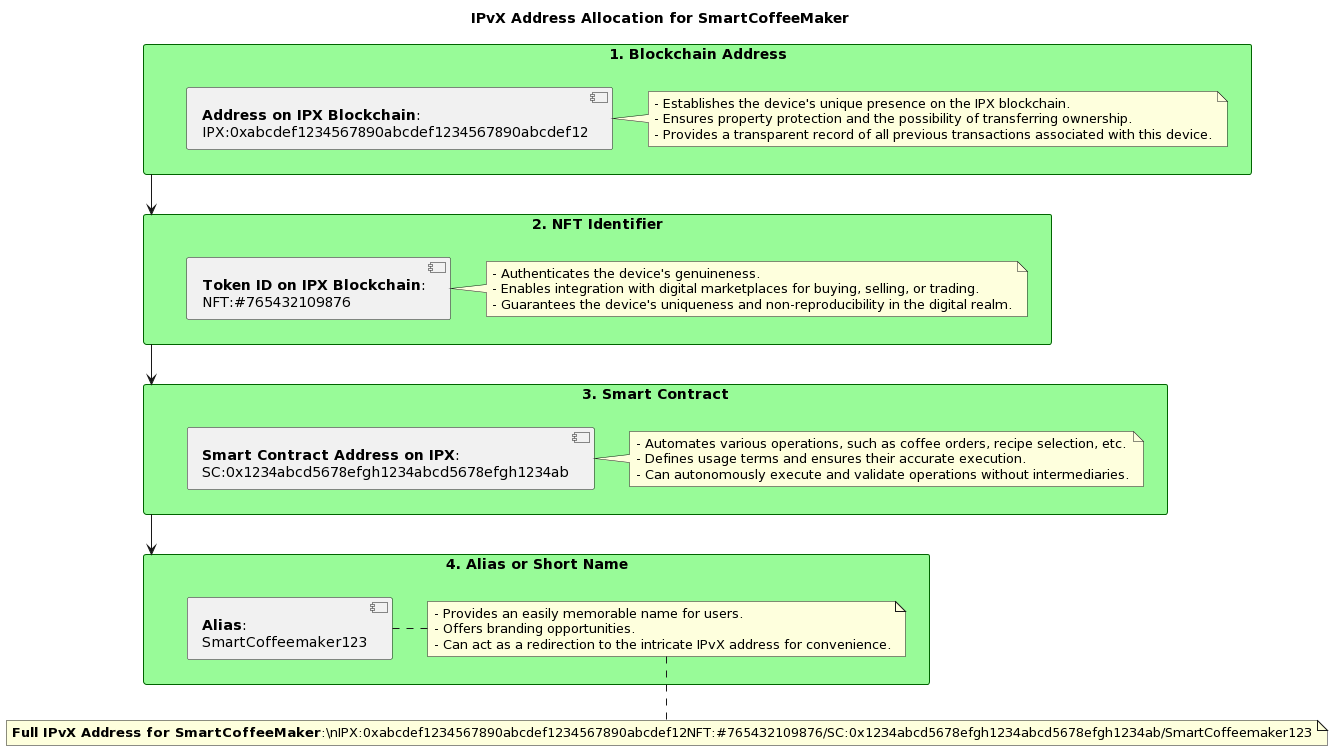
Diagram 16. IPvX Address Allocation for SmartCoffeMaker.
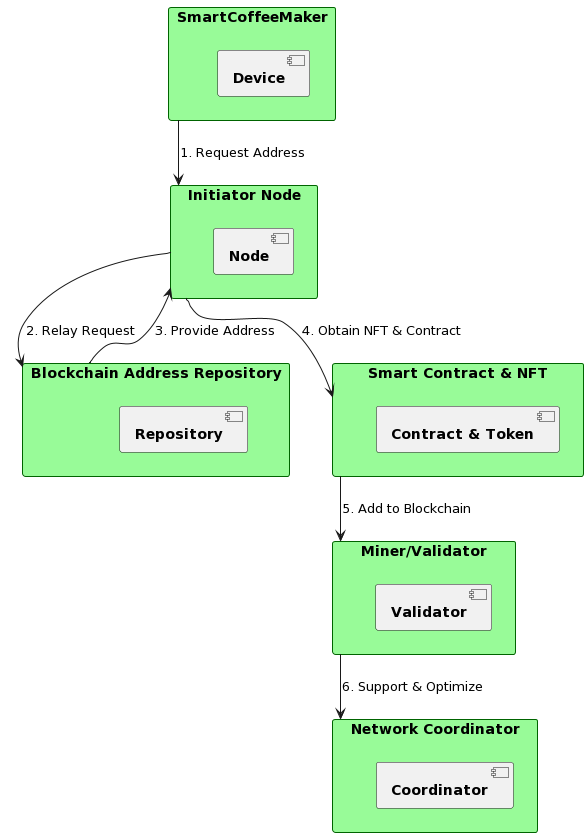
Diagram 17. To connect the SmartCoffeMaker to an IPvX network.
Example of IPvX address allocation for the Website: ImaginaryArtGallery
1. Blockchain Address:
This address locates the website’s main identity on the IPX blockchain. It’s akin to a physical address in the real world. By querying this address, you can fetch all essential metadata about the website.
{
IPX:0x1234567890abcdef1234567890abcdef12345678
}
2. NFT Identifier:
This represents the unique digital identity or certificate for the website. It ensures that the website has a distinct representation, and it can’t be duplicated within the blockchain network.
{
NFT:#987654321
}
3. Smart Contract:
A smart contract governs the functionalities, behaviors, and rules associated with accessing and interacting with the website.
Smart Contract Address on IPX:
{
SC:0xabcdefabcdefabcdefabcdefabcdefabcdefab
}
4. Alias or Short Name:
To simplify user access, an alias or pseudonym is used. This is a user-friendly identifier.
Given the above, a comprehensive IPvX address for the ImaginaryArtGallery website might look something like this:
{
IPX:0x1234567890abcdef1234567890abcdef12345678NFT:#987654321/SC:0xabcdefabcdefabcdefabcdefabcdefabcdefab/ImaginaryArt
}
Example of IPvX address allocation for a car:
SmartCar Model S
1. Blockchain Address:
This address anchors the car’s primary identity on the IPX blockchain. It’s analogous to a physical address in the real world.
{
IPX:0x1234abcd9876efgh1234abcd9876efgh1234ef
}
2. NFT Identifier:
Represents a unique digital identity or certificate of the car. It ensures a distinct representation of the vehicle on the blockchain network.
{
NFT#876543210123
}
3. Smart Contract:
The smart contract governs the functionalities, behaviors, and rules related to accessing and interacting with the car.
Smart Contract Address on IPX:
{
SC:0x5678efgh1234abcd5678efgh1234abcd5678gh
}
4. Alias or Short Name:
For user-friendly access, an alias or short name is used. It’s a more human-readable identifier.
Thus, based on the above, the complete IPvX address for the “SmartCar Model S” might look something like:
{
IPX:0x1234abcd9876efgh1234abcd9876efgh1234efNFT#876543210123/SC:0x5678efgh1234abcd5678efgh1234abcd5678gh/SmartCarModelS
}
Example of IPvX address allocation for a mobile phone:
UltraPhone Z5
1. Blockchain Address:
An address on the IPX blockchain that identifies the mobile phone’s primary identity.
{
IPX:0x5678efghabcd1234efgh5678efghabcd1234gh
}
2. NFT Identifier:
Gives the phone a unique digital identifier or certificate ensuring the device’s distinctiveness on the network.
{
NFT#543210987654
}
3. Smart Contract:
This governs the functionalities and rules about accessing and interacting with the mobile phone, including software updates, data permissions, and user privileges.
{
SC:0x1234abcd5678efghabcd1234efghabcd5678cd
}
4. Alias or Short Name:
This is a more user-friendly access name for the mobile device.
So, putting it all together, the complete IPvX address for the “UltraPhone Z5” might be constructed as:
{
IPX:0x5678efghabcd1234efgh5678efghabcd1234ghNFT#543210987654/ SC:0x1234abcd5678efghabcd1234efghabcd5678cd/UltraPhoneZ5
III. Transition from DNS to NFT Identifiers in IPvX
A. Comparison between DNS and NFT identifiers.
The traditional Domain Name System (DNS) [2] has been the backbone of the Internet for many years, serving the function of translating user-friendly records in the form of domain names into machine-understandable IP addresses.
Relying on a hierarchical and centralised structure in which domain names are mapped to IP addresses, the DNS performs its task quite effectively, but it has vulnerabilities, such as susceptibility to DNS spoofing and other cyber-attacks [15][18].
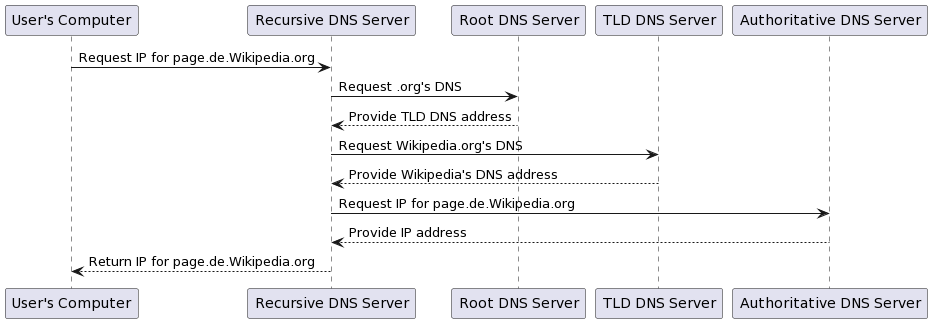
Diagram 18. DNS query traversal process for page.de.wikipedia.org.
This diagram shows a simplified view of the DNS lookup process. Real-world operations may include caching mechanisms and other optimisations to make the process more efficient.
NFT identifiers in the IPvX ecosystem represent a complete overhaul of how search queries are formed and transformed from human-readable form to numerical code and back again.
Unlike domain names, NFTs are unique, immutable and stored on the blockchain, ensuring that each identifier is unambiguous. Each resource on the network can have its own identifier, eliminating the risk of duplication or spoofing.
The IPvX system, as we have presented it with NFT identifiers, is expected to be different from the traditional DNS lookup process. Given the limited details we have outlined, let us consider a potential query process for IPvX:
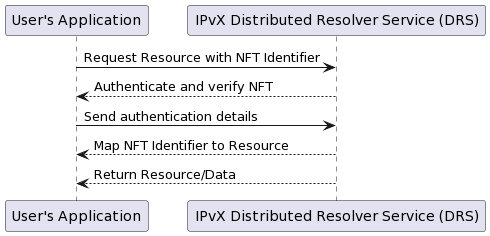
Diagram 19. The query process for IPvX.
It is important to realise that this diagram is one version and is based on our current understanding of how an IPvX system might handle NFT identifiers. The actual implementation may be different due to various technical, security and operational considerations.
The main difference between the traditional system and the proposed technology is that the traditional system is centralised and hierarchical in nature, and as a result it generates a whole heap of technological, organisational and bureaucratic costs. The new system significantly simplifies the application procedure by excluding from it a whole segment of decisions that simply become superfluous as a result of its use.
The democratic nature of the formation of such requests in general not only eliminates the technological entropy resulting from a large number of entities such as TTL domains, but also removes from the process any abuse caused by the human factor. 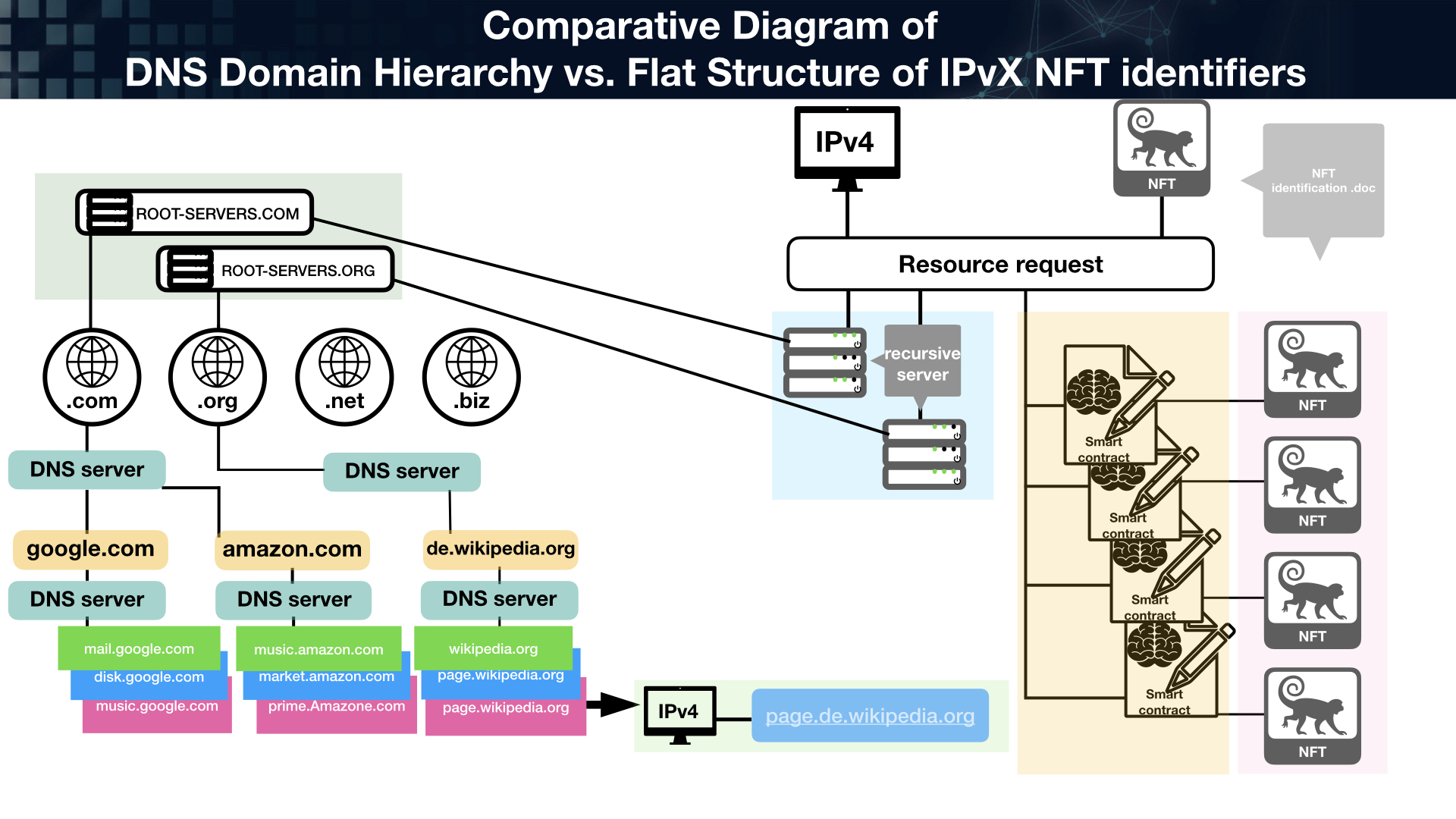
Diagram 20. The diagram compares the complexity of requests in the existing and the new system.
B. Advantages of using NFT identifiers instead of DNS.
Improved security: With NFT identifiers, risks such as DNS spoofing are virtually eliminated. The blockchain-based nature of NFTs ensures that they can’t be altered or tampered with [16].
Decentralisation: Unlike the centralised DNS, NFT identifiers operate on a decentralised model, eliminating single points of failure and increasing resilience [36].
Transparency and traceability: Every transaction involving an NFT identifier is recorded on the blockchain, providing an immutable history of its interactions [6][11].
Scalability: The IPvX ecosystem using NFTs potentially allows for a greater number of unique resources, adapting to the ever-expanding Internet domain [7].
Control and tradability: NFTs can represent ownership or access rights that can be traded, potentially creating a new market for Internet resources [37].
C. Examples of how NFT identifiers work in an IPvX network.
Resource access: A user sending a request for a resource can be directed to it using its unique NFT identifier. Through a decentralised lookup service (which we will discuss in the following sections of the paper), the corresponding NFT identifier is located and the user is granted access. This process is transparent, secure and verifiable at every step [34][36].
Transferring ownership of the resource: In scenarios where resources need to change hands, the associated NFT identifier can be transferred to a new owner, similar to transferring ownership of a digital artwork or other asset represented by an NFT [12].
Resource trading: Under market conditions, NFT identifiers can be offered for sale. A user wishing to sell access rights to a particular resource can specify an NFT identifier, and another user can buy it, thereby obtaining access rights to that resource [11][37].
D. NFT identifiers as a system for obtaining information about a host in IPvX.
Like Whois, whose main purpose is to obtain registration data about the owners of domain names, IP addresses and autonomous systems, and which essentially contains knowledge about the state of a host [1], the NFT identifier, which is an integral part of an IPvX address [5], carries even more complete information about the host [6], without requiring the creation of a separate Internet protocol that gathers information from various sources to produce a state report [2].
All you need to know about the current state of the host is in the NFT identifier, which can contain information about any Internet resource, be it websites, documents, videos, etc [6].
Here are some examples of NFT identifier content:
1. Basic information:
– Resource name: An analogue of a domain name or website/application name [2].
– Resource type: Identifies whether the resource is a web page, document, video, image, etc [6].
– Creation Date: Indicates the date the resource was registered or created [3].
– Last updated: Indicates when the resource was last updated or modified [3].
2.Specifications:
– IPvX Address: Unique address of the resource on the network [5].
– Protocol Type: The resource can be accessed via HTTP, HTTPS, FTP, etc [4].
– Resource Location: Information about the physical server or cloud storage where the resource is hosted [9].
3 Organisation and contact details:
– Resource Owner: Name of the person or organisation that owns the resource [10].
– Contact Information: Email address, phone number, physical address, etc [11].
– Administrative Contact: The person or organisation responsible for managing the resource [11].
4. Blockchain-enabled attributes:
– Ownership history: An immutable record of all previous owners or transactions associated with the resource [12].
– Authentication: Digital signatures or other mechanisms that guarantee the authenticity of the resource [13].
– Associated rights: Details of licensing, use, access or modification rights [14].
– Metadata: Additional information such as tags, categories or descriptions associated with the resource [15].
The move to NFT identifiers in the IPvX architecture not only addresses the weaknesses and limitations of traditional DNS [18], but also creates a more transparent, decentralised and rich information structure for network resources [16]. This provides greater trust, clarity and potential functionality that the Internet of the future may require [17]. 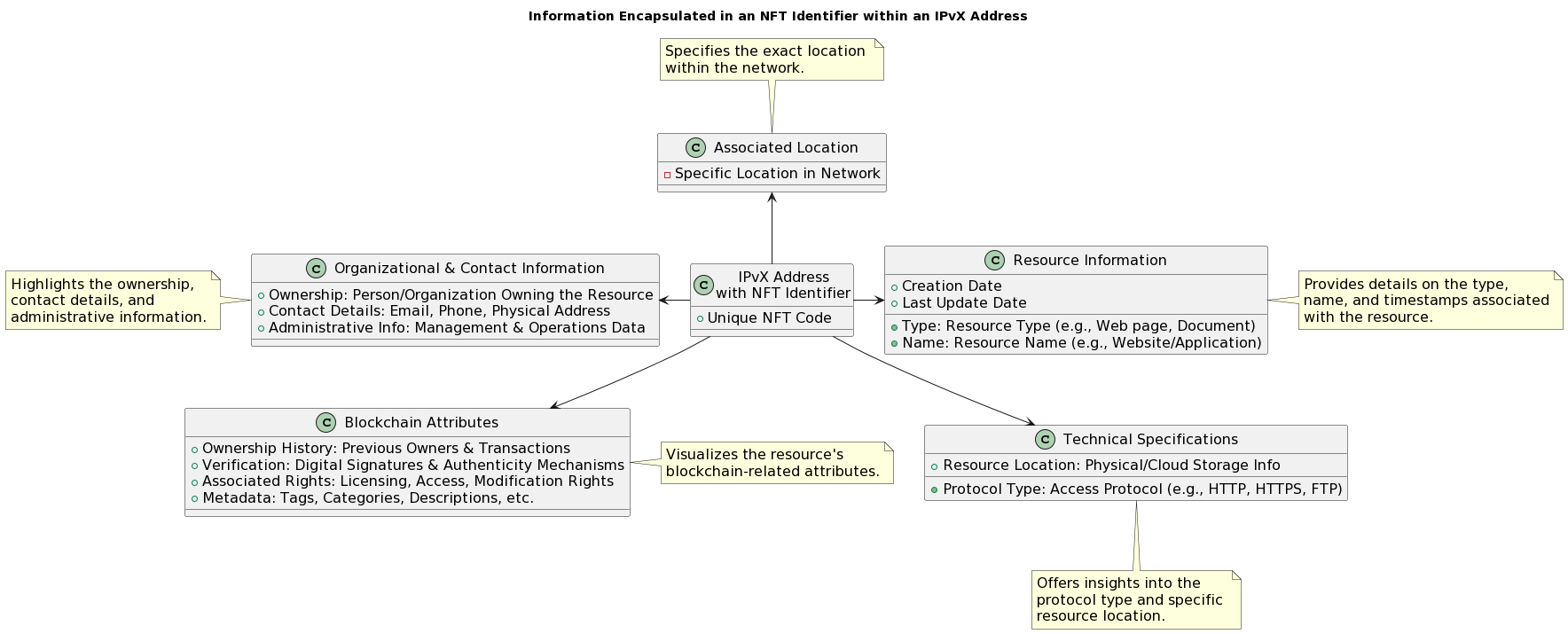
Diagram 21. Illustration of the information encapsulated in an NFT identifier in an IPvX network.
The transition from traditional DNS to NFT identifiers in IPvX opens up a new approach to discovering, accessing and managing network resources on the Internet. As the digital sphere continues to evolve, the adoption of IPvX will be the key to a safer and more efficient digital future [5].
IV. Authentication in DNS and IPvX: a comparative analysis.
One of the most important elements of any infrastructure is the authentication process, which is a critical element in ensuring security and reliability on the Internet.
In this section we will compare the authentication process in the traditional DNS system and the IPvX system we are designing.
How the authentication process is carried out in these systems will be crucial in evaluating their advantages and disadvantages [1][5].
A. DNS authentication.
Traditional but necessary
Trust through hierarchy: At the heart of DNS technology is a hierarchical structure of root servers, which at the top of the system dictate trust down the hierarchy, ensuring that only authorised entities make updates [2][3]. 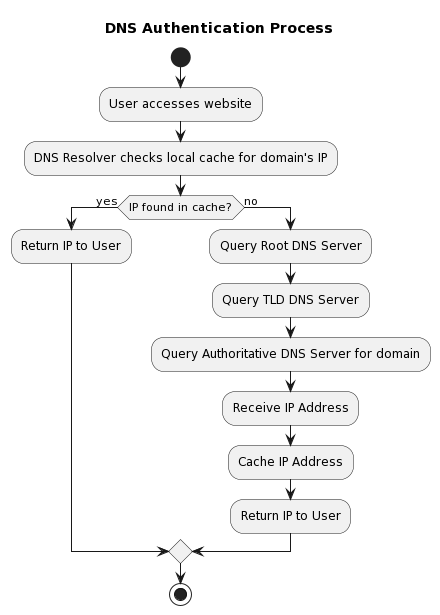
Diagram 22. DNS Authentication Process
Zone transfer: When secondary DNS servers require updates, they typically request a zone transfer from the primary server. While effective, this mechanism can be vulnerable if not properly secured [18][19].
Security Extensions (DNSSEC): As part of the evolution and in response to vulnerabilities, the IT industry has introduced DNSSEC technology. This extension provides authentication of DNS data, ensuring its integrity and authenticity of origin. However, despite its effectiveness, its use requires the decision of the network administrator, and as a result its use is not widespread, leaving many domains on the network unprotected [15][21].
B. IPvX authentication using NFT.
Innovative and Decentralised
Decentralised trust: Unlike the hierarchical structure of the DNS, IPvX relies on a decentralised consensus mechanism available in the blockchain. With this mechanism, every node in the network verifies transactions, reducing the number of points of failure [5][6].
NFT as unique identifiers: Each resource or node in the IPvX network has a unique NFT identifier that confirms the right to use it, in addition to recording the device type and its owner on the blockchain. This ensures not only that the resource is unique and can be uniquely authenticated, but also “the ability to verify the legitimacy of its use” [6][11].
Automation of smart contracts: The integration of smart contracts into the IPvX ecosystem provides an automated and trusted method for authentication procedures. Any action associated with an NFT identifier can be pre-defined and executed without centralised oversight, as the request matching function is verified by the smart contract in which it is defined, which in turn provides transparency and protection against unauthorised access without additional third-party verification [7][16].
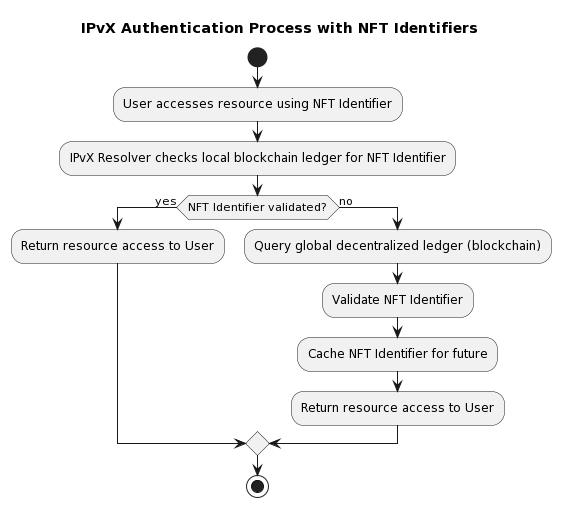
Diagram 23. IPvX Authentication Process with NFT Identifiers.
C. Comparative analysis.
Single Point of Failure vs. Decentralisation:
DNS – Due to its hierarchical nature, it can have potential infrastructure vulnerabilities in the form of single points of failure, especially if root servers are compromised.
IPvX – In contrast, the decentralised IPvX approach distributes trust to all nodes with access to blockchain records, greatly reducing such vulnerabilities [1][5].
Manual control vs. automation:
DNS – requires manual configuration and control, especially for zone transfers, which can lead to human error.
IPvX – provides automation through the integration of smart contracts, virtually eliminating the possibility of misconfiguration [3][7].
Use of security protocols:
DNS – although DNSSEC provides enhanced DNS security, its use is not ubiquitous.
IPvX – has embedded advanced mechanisms using cryptography that provide a consistent level of security across the network [15][21][16].
Conclusion:
Comparing the authentication approaches used in DNS and IPvX, the following conclusions can be drawn:
DNS relies on hierarchical methods that are a direct consequence of the mechanisms used in the existing Internet model.
IPvX, on the other hand, uses decentralised and automated methods based on the capabilities of blockchain and NFT technology [9][12].
The obvious advantage of decentralised mechanisms over hierarchical systems leads us to further explore the topic of transition from the existing hierarchical domain structure to a decentralised one.
V. Transformation of Domain Structures in the IPvX Ecosystem
Introduction.
As we have previously noted in the existing structure of the Internet, the Domain Name to Digital Value System (DNS) provides a hierarchical model for classifying web resources into first, second, third level domains and so on [2].
The procedure of a search query for a website address goes through the entire sequential chain of DNS servers that direct the user to the desired resource.
This hierarchical system is intuitive and logical; for example, a domain structure such as `blog.example.com` points directly to the blogs section of the main site `example.com` and so on [18]. Our IPvX Ecosystem project, accompanied by the introduction of non-fungible token (NFT) identifiers, radically changes this long-established hierarchical structure [6]. 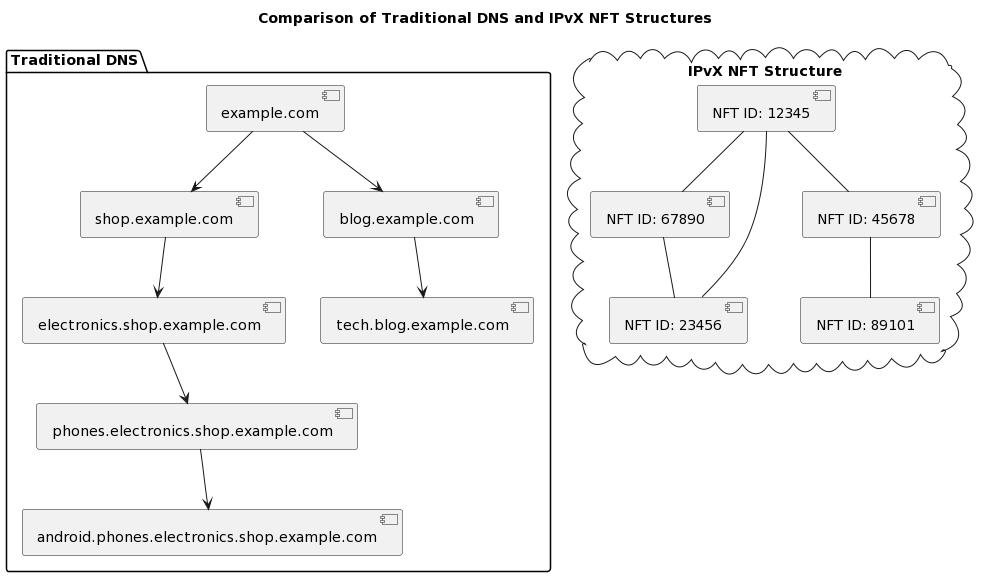
Diagram 24. Comparison of traditional DNS and IPvX NFT structures
A. Why does IPvX not use domain names directly?
The design of IPvX is based on the principles of decentralisation, security and immutability, implemented through the use of unique NFT identifiers [6]. The use of the current domain name system, which is centralised and vulnerable, is completely contrary to these principles [13]. While domain names are important for ease of recall and branding, they cannot match the security, uniqueness and tradability that NFT provide [16].
In addition, it should always be remembered that the current domain name system does not offer users ownership of their name, but rather a temporary use, a lease that can be terminated, for example, by a decision of government regulators or registrars. Unlike the domain structure, the use of NFT identifiers guarantees the resource owner that no one can take their property without their consent.
Within the complex structure of the IPvX ecosystem, domain names can certainly be used and linked to NFT identifiers for the convenience of users, but they do not replace these innovative identifiers on the blockchain [7]. They will essentially act as pseudonyms or labels, but will not carry the legal and regulatory burden. 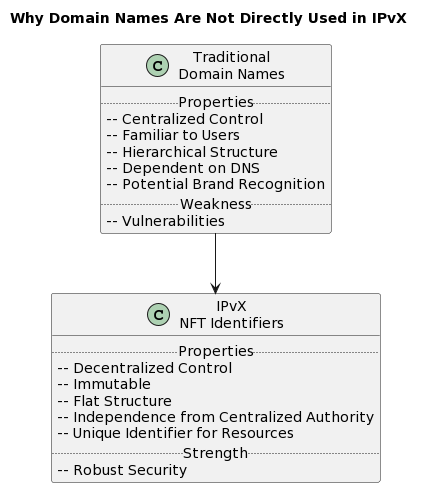
Diagram 25. Why domain names will not be used directly in IPvX.
B. Transition from Hierarchical Domains to Flat NFT Identifiers.
The design of IPvX is fundamentally different from the traditional hierarchical domain structure [2]. Instead of nesting resources in parent domains, the IPvX ecosystem introduces a flat, decentralised structure based on unique and immutable NFT identifiers [6].
In this system, each resource has its own unique NFT identifier. For example, what is known in the DNS as blog.example.com is given an independent NFT identifier in IPvX, unrelated to its traditional parent domain example.com [18].
This transition has several advantages:
Decentralisation and security: each resource is assigned a unique identifier that guarantees its autonomous operation, strengthening security and avoiding the vulnerabilities of traditional hierarchical DNS systems [15].
Flexibility in resource management: individual resources can be managed, sold or monetised without affecting the parent domain or other related entities [11].
Transparency: thanks to the blockchain design, each identifier and its associated changes remain transparent, immutable and easily verifiable [12].
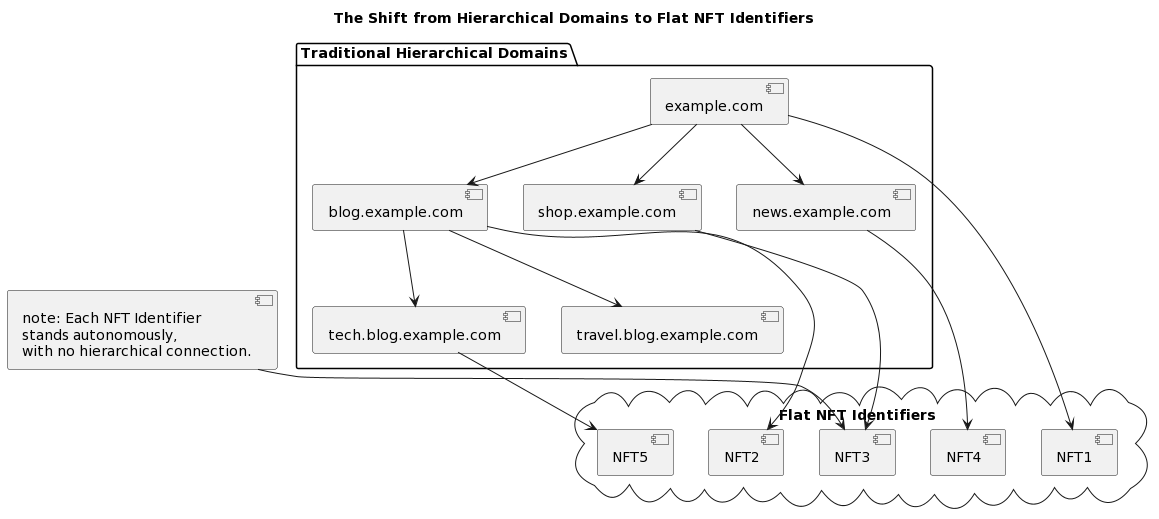
Diagram 26. Moving from hierarchical domains to flat NFT identifiers.
However, this new approach has its own challenges. Both users and developers used to the familiar DNS hierarchy [2][3] must adapt to this new way of organising and managing resources [6][17].
To ease this transition, specialised tools and interfaces designed to explain the relationships between individual resources, even without traditional hierarchical relationships [17][33], may become available in the IPvX ecosystem.
C. Implications for User Interaction and Resource Discovery.
Moving from a hierarchical domain basis to a flat NFT identifier structure fundamentally changes the mechanisms for user interaction and online resource discovery [6][11].
While there are obvious benefits in terms of improved security, increased transparency and new commercial opportunities [6][16], the system also introduces fundamentally different methods of navigation and resource accessibility for users [37]. Without the familiar hierarchical scheme, there is a need to develop new tools and techniques to simplify resource discovery and access [6].
Similar to the development of search engines in response to the growth of the Internet, the IPvX environment may be the impetus for the emergence of advanced AI-based tools to help users navigate this new digital landscape characterised by unique NFT identifiers [36]. 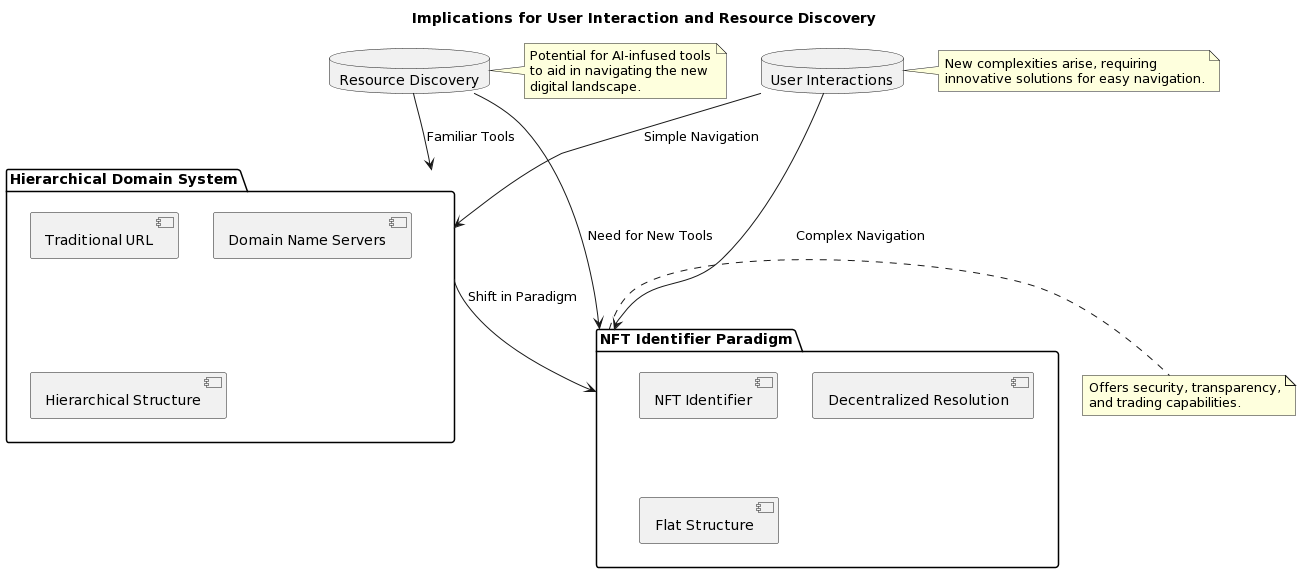
Diagram 27. Implications for user interaction and resource discovery.
Conclusion.
With the introduction of NFT identifiers, the IPvX ecosystem is changing some of the fundamental tenets of the Internet’s existence [5][6]. This change ushers in a new era of enhanced security, transparency and transactional capabilities [9][12].
However, we also face new challenges: how to ensure simplicity and ease of navigation in such an environment? The answer to this question is presented in the next chapter, where we look at the introduction of new navigation implementation tools, including DRS, a decentralised resolver service, which will be a key element in ensuring a smooth transition and intuitive use in the new IPvX ecosystem.
VI. Navigating a Distributed Network: The Role of the Distributed Resolver Service in IPvX.
Introduction.
To realise the transition from a hierarchical Domain Name System to a flat network of NFT identifiers [6], a key component of the IPvX ecosystem, the Distributed Resolver Service (DRS), comes to the fore.
This is a fully decentralised mechanism that exploits the properties of flat network nodes, such as reliability, availability and interchangeability, to provide almost instantaneous reliable information about the location of the requested resource [17].
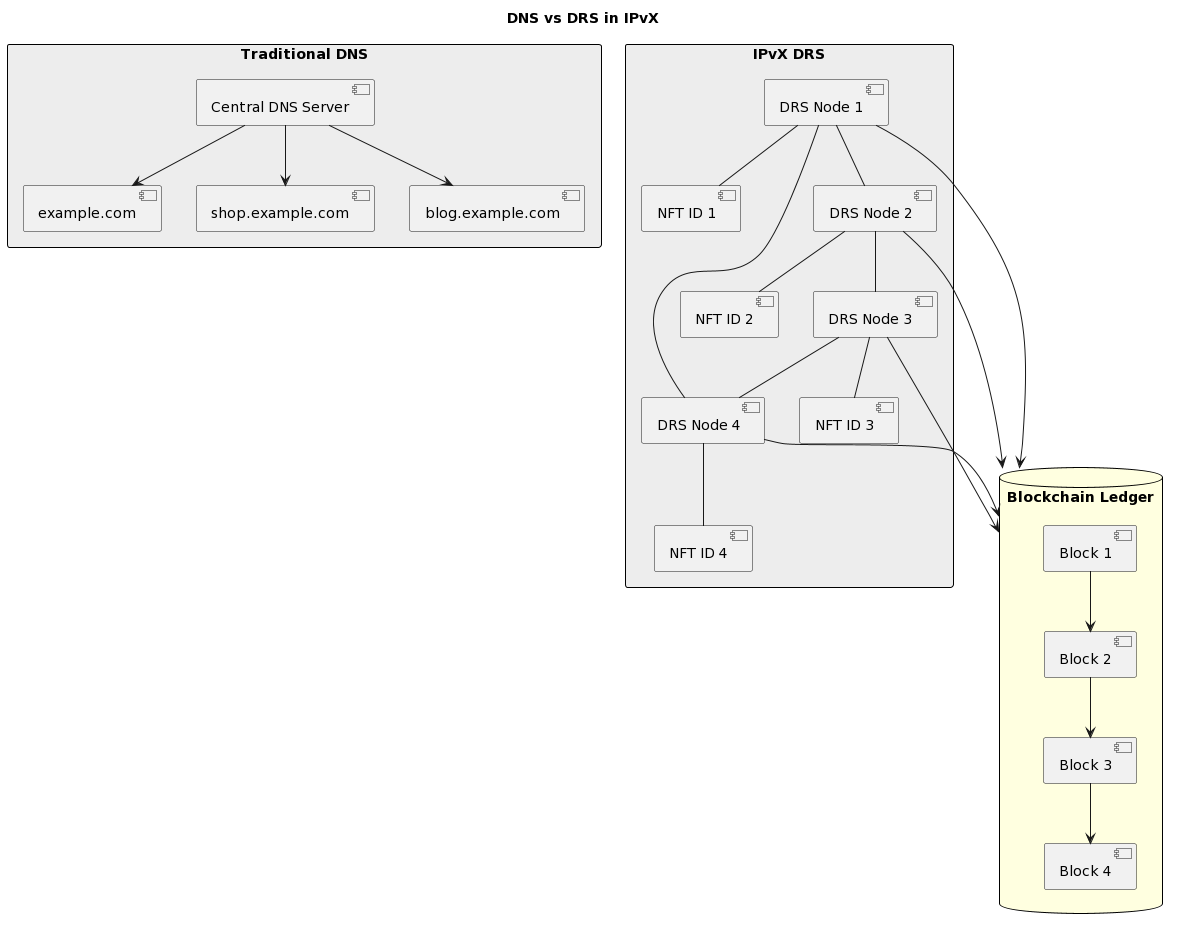
Diagram 28. Traditional Model vs. IPvX Model
A. The Essence of the Distributed Resolver Service in IPvX
In the IPvX space we are creating, the DRS service acts as a skeleton that must provide a seamless connection between network users and the resources they request. Its primary function is to route user requests directly to the NFT identifiers that are part of the IPvX address associated with the requested network node.
Unlike the centralised channels of traditional DNS servers, DRS operates in a Distributed manner. Decentralised nodes collectively manage resource requests; any available resolver can accept and route the request to a node, providing transparency, security and no centralised management vulnerabilities [7][16]. 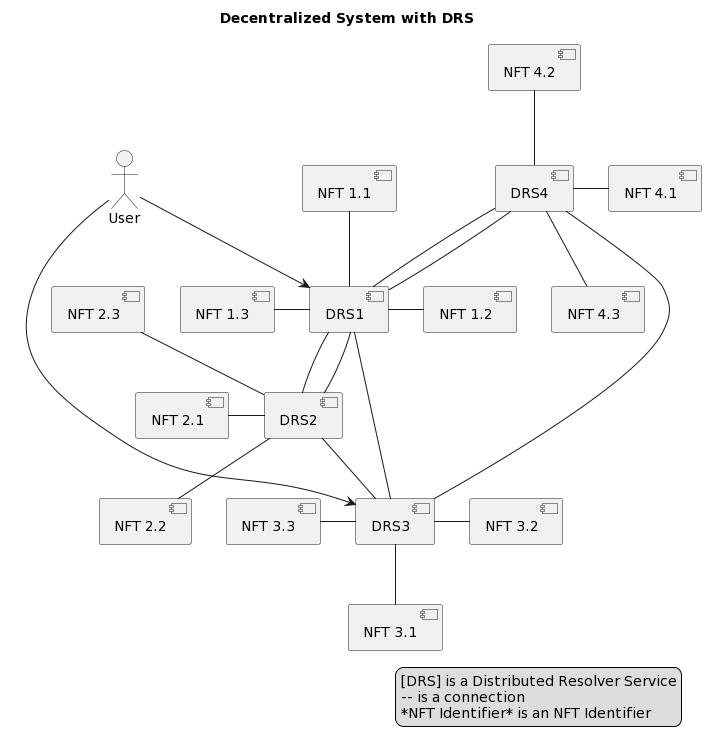
Diagram 29. Decentralized System with DRS
B. Queries via DRS in an IPvX system
The IPvX system uses the Distributed Resolver Service (DRS) as a key component to manage queries in its distributed environment. The following is a description of this process [10][11]:
1. User Initiation: In IPvX, a request begins with a user or application seeking access to a particular resource. Each resource in an IPvX network is associated with an NFT identifier as part of the node address.
In this sense, an NFT can act not only as a token confirming ownership of content located on a given node, but also as a unique reference to a resource [6], since it contains a unique numerical code.
2. Smart contract generation: The initiated request containing the requested NFT identifier generates a smart contract describing the basic terms contained in the request. This step ensures the legitimacy of the request and protects the integrity of the associated data [12].
3. Decentralised transmission: Next, the request is propagated through the IPvX network and reaches the distributed resolver nodes. Each of these nodes is capable of interpreting the encoded request and identifying the corresponding NFT [5].
4. Consensus-based validation: An inherent feature of distributed systems is consensus-based validation [13]. When a request is received, the nodes that make up the DRS cross-validate it against pre-defined criteria defined by the smart contract of the request. This collective validation acts as a defence against possible malicious attempts by ensuring that only valid requests are executed.
5. Reply transmission: After successful validation, the requested node, which stores the relevant data, processes the request. The received data or resource is sent back, decoded and presented to the user or application [14].
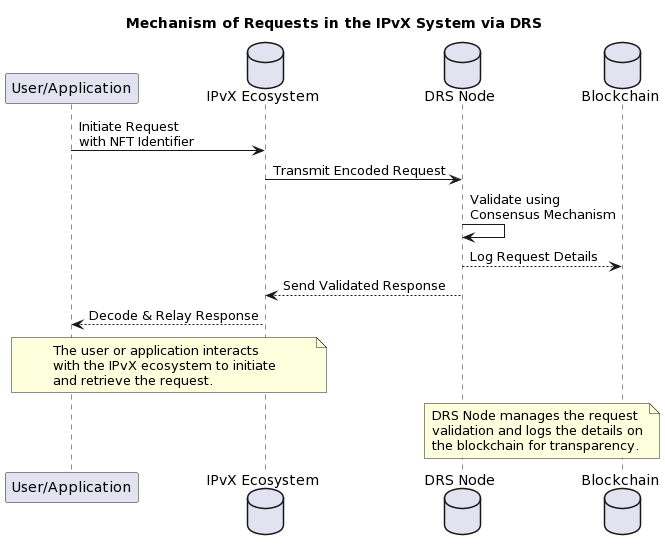
Diagram 30. Request processing mechanism in an IPvX system using DRS
The implementation of DRS in an IPvX environment provides an optimised, secure and efficient request and response mechanism [8][15]. The service takes advantage of decentralisation by providing a reliable platform for requesting and receiving resources, while eliminating the risks associated with centralised systems.
This is particularly evident when we consider the illegal side of the modern Internet, the so-called “Darknet”, which exploits all the weaknesses of the existing hierarchical domain name system for the benefit of black and grey market criminals.
C. Integration of Smart Contracts in DRS in the context of the IPvX system
Smart Contracts in the context of the IPvX system are fundamental elements that automate and strengthen the request and response processes in the DRS [7]. How they work is described below:
1. Smart Contract Activation: A user request associated with an NFT identifier can activate a specific smart contract that describes the conditions for performing a given action in the IPvX system.
2. Unified processing in DRS: Once activated, the smart contract is analysed and executed by nodes within the DRS. The deterministic nature of smart contracts ensures a consistent and unified process across all nodes.
3. Authentication protocols: The smart contract has built-in authentication procedures that we discussed above. If certain permissions or criteria are required to access a resource, the contract evaluates these conditions. Only if all the specified conditions are met will access to the resource be allowed.
4. Every interaction within a smart contract, from the initiation of a request to its authorisation, is recorded on the IPvX blockchain. This provides a permanent, immutable record that can be referenced for accountability and transparency.
5. Operational efficiency: Smart contracts in the DRS context automate several steps in the request-response cycle, eliminating intermediaries. This increases the efficiency of the system in terms of both time and potential cost.
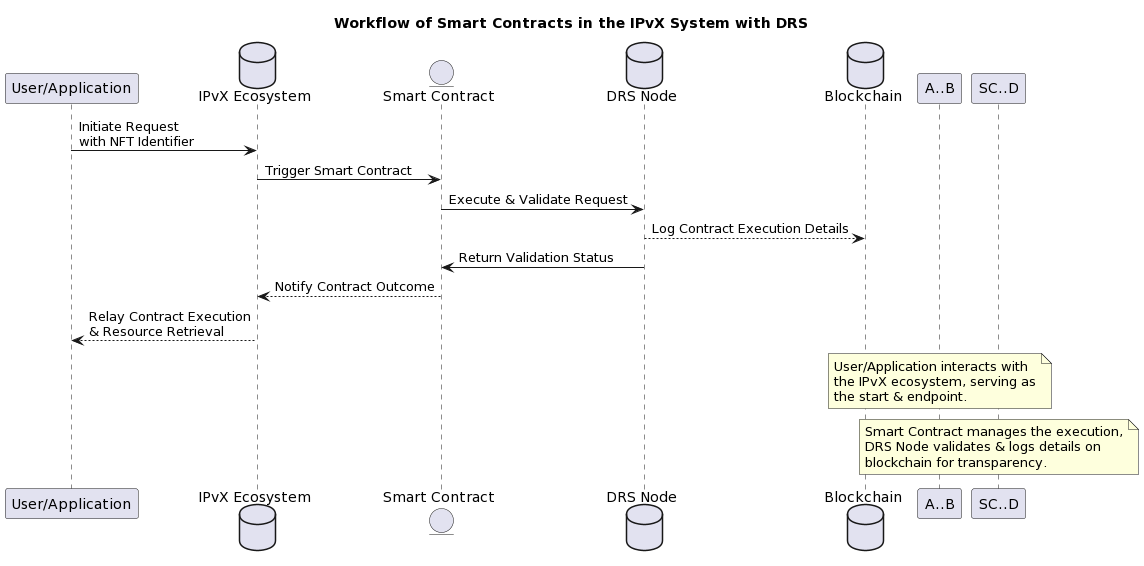
Diagram 31. Diagram of how smart contracts work in an IPvX system with DRS
The use of smart contracts and DRS in an IPvX system creates a stable, transparent and efficient mechanism for handling requests, ensuring non-interference by third parties and accurate execution. This combination leverages the strengths of blockchain technology, providing optimised operations and enhanced system security.
D. Superiority of DRS over traditional DNS.
The Distributed Resolver Service has a number of design and implementation advantages over its DNS counterpart [17][18]:
1. Decentralisation at the core: The DRS structure itself is decentralised. This design contrasts with the centralised DNS model by providing a structure that is resilient to single points of failure.
2. Enhanced protection: DRS, with its decentralised DNS, provides robust protection against threats such as DDoS and DNS spoofing, which cause permanent, colossal damage to users of the traditional DNS system.
3. Transparent records: Every authorisation or transaction in the DRS system is meticulously recorded using blockchain transparency. This ensures immutability and transparency of records, which is invaluable for audit trails and system integrity.
4. Scalability at its core: The decentralised structure of DRS inherently supports scalability. As the network grows, all new nodes can be easily integrated without the traditional problems of centralisation or performance lock-in.
5. Elimination of centralised chains: The DRS operates independently of centralised control bodies such as ICANN and first-level domain zone registries, which will obviously enable a truly democratic Internet with equal rights for all members, not subject to singular control or censorship [32][33].
Conclusion:
The distributed resolver service in IPvX represents an evolutionary step towards a future where NFT identifiers dictate resource mapping [34][35]. This transition not only supports the principles of decentralisation, but also promises a new digital landscape that is secure, transparent and optimised for the challenges of tomorrow.
VII. Navigating Tomorrow: The Domain Name Perspective in the IPvX Ecosystem
Introduction
If the IPvX project using NFT identifiers is successful, the question of the future of the existing domain industry [2][18] will inevitably arise. Will it coexist unchanged alongside the new ecosystem, transform into something new, or gradually become obsolete? we will explore this in this chapter.
A. Possible developments.
Parallel Coexistence
As IPvX technology develops and evolves, and NFT identifiers are used to direct the user’s request [6], it is possible that coexistence with traditional domain names will occur. These familiar domain structures can serve as mnemonic bridges to the corresponding NFT identifiers, providing a combination of old and new.
Domains using NFT:
Since each domain name is unique, they can be represented as NFTs in the IPvX system [6]. This metamorphosis will allow domain names to play a dual role – serving users as familiar web pointers and realising the full functionality of NFTs as assets.
Smart contract domains:
The introduction of smart contracts into the domain equation can lead to combined domain names with built-in logical capabilities [7]. These include automatic redirection of queries based on conditions, dynamic content representation or domains that adapt in real time.
Decentralised domain marketplaces:
NFT-based IPvX could lead to decentralised domain markets [6]. Domains will not just be addresses, but commodities that can be traded and exchanged in secure zones without intermediaries.
B. Problems and solutions.
Problem of transition to DRS:
The mass use of the DNS system will definitely resist the transition to the DRS model [3][19], especially since this will strangely affect two completely opposite sides.Such an implementation will definitely not be to the liking of the current domain addressing bureaucracy and its DarkNet antagonist.
Action needed:
The introduction of the new technology should be obvious to the broad mass of users and will definitely require a lot of education. However, it will be important to motivate the use of the new technology to eliminate the constant threats emanating from the network, which will significantly reduce the cost of maintaining security specialists and reduce the damage caused by unauthorised actions by criminals.
The problem of technical integration:
The use of DRS technology will inevitably face problems of technological integration with existing network devices and the personnel operating them [6][17].
Necessary actions:
A rapid and widespread transition to the new infrastructure will require the development and adoption of the necessary RFC standards by the IETF technology expert community, as well as close co-operation with network and northbound hardware and software developers.
Financial implications:
The introduction of the new system will clearly disrupt the established domain registration economy, which employs tens of thousands of people worldwide [8].
Required actions:
Transitional financial strategies need to be developed so that the transition from the existing financial structure operating the DNS allows domain industry professionals to rethink business models and find an interface with the emerging DRS and NFT identifier system.
Regulatory issues:
System changes raise potential regulatory and governance issues [9] as they need to be rethought and rebuilt. In addition, the role of government in managing national domain registries will disappear, which will undoubtedly cause some resentment among the bureaucrats who maintain the system.
Action needed:
The only way forward here will be to convince regulators that the system being designed is secure from the user’s point of view and transparent, which will prevent the development of various abuses. It also has huge economic and technological potential, which will generate more revenue for the state and its citizens. But the other side of the coin is the impossibility of state censorship and blocking of resources. Which, of course, will not please everyone.
C. Comparison with alternative evolutionary paths.
In this section we will compare existing developments in the transition from the existing domain structure to decentralised domains using WEB 3.0 technology with our planned IPvX system [6].
Decentralized Domains:
Let’s start with a brief overview of alternative systems on the market
Notable projects in this area include Unstoppable Domains, Handshake, Ethereum Name Service (ENS), freename.io, Bonfid, PeerName, Namecoin, Blockstack, quik.com, Emercoin and NEMDNS [7][17][32].
Below you will find a diagram and a description of the approximate functionality of such a system. 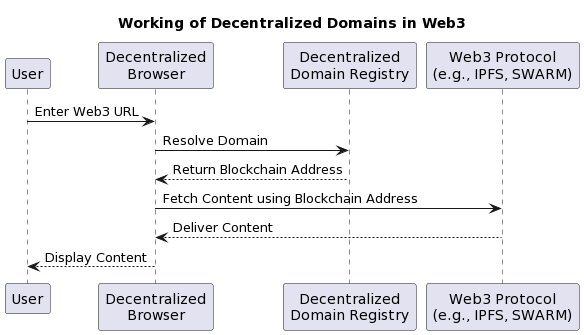
Diagram 32. Working of Decentralized Domains in Web3
In this diagram of action sequences:
1. The user enters a Web3 URL in the remote browser.
2. The remote browser queries the remote domain registry to resolve the domain entered.
3. The decentralised domain registry returns the associated blockchain address to the browser.
4. The browser then retrieves the content associated with that blockchain address using Web3 protocols such as IPFS or SWARM.
5. The Web3 protocol returns the content to the browser.
6. Finally, the browser displays the content to the user.
A similar process can be seen in the IPvX ecosystem in the following diagram:
This sequence diagram provides a linear view of the interaction, allowing us to understand how each component interacts with the others in the process.
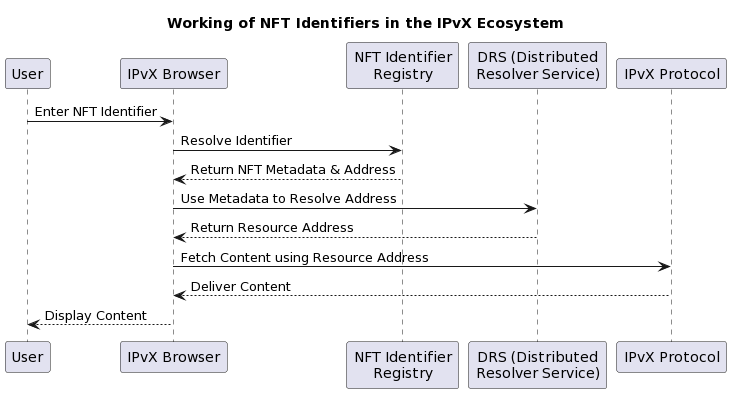
Diagram 33. Working of NFT Identifiers in the IPvX Ecosystem.
Now compare the two diagrams:
Domain resolution:
Web3: Decentralised domains in Web3 require a browser to query a decentralised domain registry.
IPvX: The IPvX system first resolves the NFT identifier to obtain metadata and the associated address.
Content Retrieval:
Web3: Direct interaction between the browser and the Web3 protocol retrieves content.
IPvX: The browser communicates with the DRS to resolve the resource address from the metadata. It then uses the IPvX protocol to retrieve the content.
Security and ownership:
Web3: Security is primarily based on the immutability and decentralisation of the blockchain.
IPvX: Incorporates the robustness of NFTs, symbolising real ownership and the security attributes that come with it.
Interactions:
Web3: Fewer interactions as it relies primarily on the decentralised domain registry and the Web3 protocol.
IPvX: More interactions, ensuring that the NFT identifier accurately represents a resource and its metadata, leading to the exact content.
By comparing the diagrams side by side, one can deduce the additional steps and security layers in the IPvX ecosystem, emphasising its uniqueness and advantages over traditional Web3 decentralised domains [14][16][32].
Let’s look at some more arguments for and against these two technologies.
Decentralized domains:
Function: Decentralized domains, built on blockchain technology, were designed to offer secure, censorship-resistant registrations without centralized oversight [12][13].
Advantages: These domains present a reduced risk of domain seizures and promise better user privacy.
Limitations: Despite their potential, they merely emulate the traditional DNS structure on a decentralized foundation [3][19].
NFTs in the IPvX ecosystem:
NFT identifiers are not just like an address – they represent an asset with intrinsic value and potential [6].
Function: Beyond simple routing, they embody ownership, validated by the immutable nature of the blockchain [12].
Benefits: Real, tangible ownership, the possibility of dynamic linking, and the organic fusion of addressing with the value of the digital asset.
Limitations: There is a problem of easy identification, analogous to domain names, which will require a solution to be discussed with the expert community. In the next chapter we will look at options to address this problem.
From a practical point of view, decentralised domains do not need to be fundamentally different from the existing system; in fact, the point of their existence is the same naming resource, just more secure and accessible through the upper layers of the network infrastructure, which is generally not very reliable from the point of view of the overall structure. In short, decentralised domains are essentially just a new packaging of the existing domain registration system.
In contrast, NFT identifiers in the IPvX ecosystem change the very nature of the digital infrastructure, encompassing a wider range of possibilities for integration with the modern technological environment, as they represent an innovative approach that treats Internet addresses as entities containing valuable assets in the form of NFT tokens.
As a result, NFT identifiers offer broad interoperability with different platforms, applications and services, which goes beyond the limited capabilities of decentralised domains.
In general, it should be noted that the IPvX ecosystem offers a general change to the existing network model by introducing the concepts of the blockchain layer, which is absent in the current OSI model, making the proposed technology fundamentally different from any attempt to renovate the existing system.
VIII. Overview of Possible Options for Accessing Nodes in an IPvX System
In a system without traditional domain names, users will of course want a simple, intuitive interface to access the nodes they know. We are not talking about searching through search engines, we are talking about a direct query to a resource known to the user, as we now address the domain example.com.
A. NFT identifier.
In a system without traditional domain names, we ideally expect users to enter a unique identifier they know in order to access a particular host. Although of course we recognise that a direct link to a resource written as an NFT token is difficult to remember or perceive, so in its purest form this is more applicable to hardware-based automated systems where direct human involvement is minimised.
In the context of IPvX with NFT identifiers, this would look like this [6]:
When communicating with a DRS system, the primary request for a resource is based on the NFT identifier. This identifier is a key part of the IPvX address, which requires each resource to be unique and non-repeatable [6].
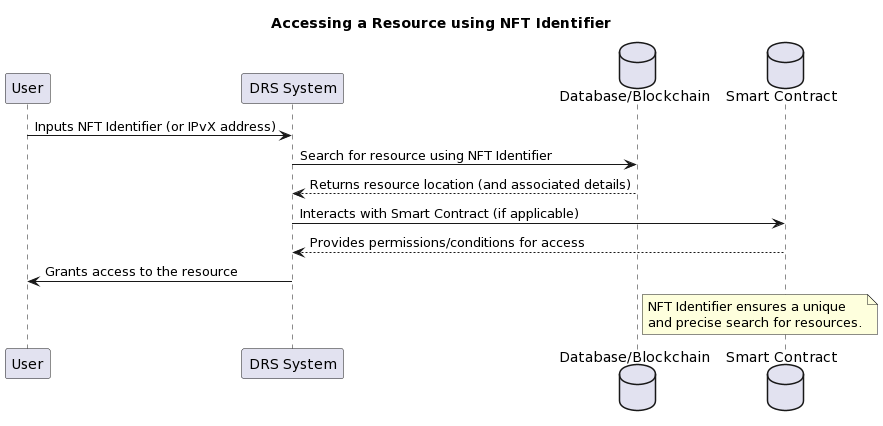
Diagram 34. Accessing a resource using the NFT identifier
The key role of the NFT identifier in the DRS system is to ensure a unique and accurate search for resources within the network.
B. Short Name or Alias.
If the system supports aliases or short names associated with NFT identifiers, users could enter them for ease of access, similar to domain names in the existing DNS system [2]. This would provide a more human-readable interaction with the direct search system.
In the case of a direct query for an identifier for a particular resource, such as a PDF document, we have a target address in the form of something like “0x1234abcd5678efgh9012ijklmno3pqr“.
In a system that supports aliases or nicknames, we can use a nickname to request it, such as @report2023. This allows us to access the document directly, without the long URL used in the traditional DNS system.
Here @ can represent the beginning of a nickname or alias.
Within this solution, two options can be distinguished for the management of short name directories:
Universal aliases: names and aliases that are the same for all users with respect to universally recognised resources (e.g. based on user voting).
Custom aliases: unique to each user. For example, a user can create their own alias for a specific resource or contact, which makes the system more flexible, but such a resource catalogue can only be used from a specific node, which should be reflected in the smart contract when a request is made.
Most likely we can use these two solutions in combination.
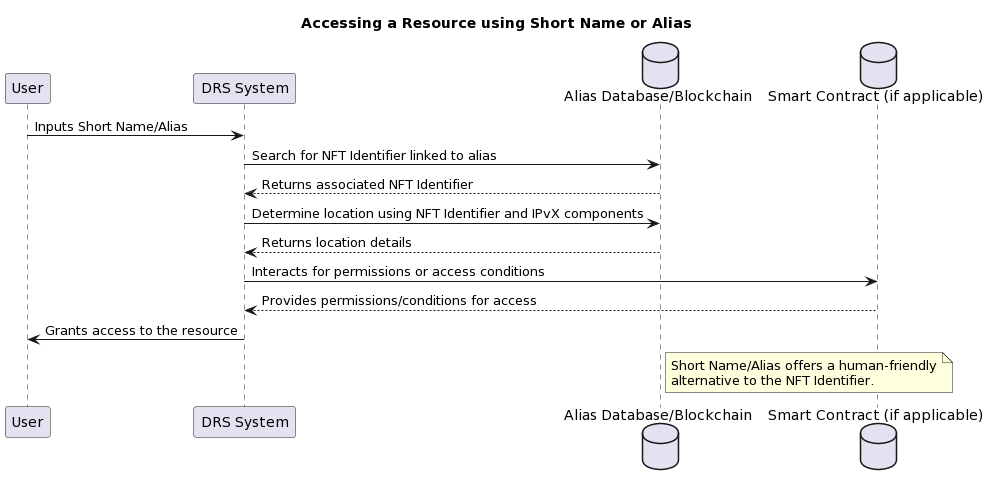
Diagram 35. Accessing a resource using a nickname or alias
Accessing a resource in DRS using a nickname or alias:
The advantage of using a nickname or alias is that it is human friendly, making it easier for the user to remember and type.
C. Decentralized URL.
The address may begin with a special scheme such as “dweb://” or “ipvx://”, indicating that it is a decentralised resource rather than a regular web address [31]. Such a special prefix emphasises the decentralised nature of the access method[32].
An example of a decentralised URL is
dweb://report2023.ipvxnetwork
Such a URL allows access to content that can be stored and shared from multiple nodes, or nodes that are resilient to failure and censorship. This is in contrast to the current model based on centralised servers, where a single server or group of servers provides content. An NFT identifier or alias can be embedded in such a URL. 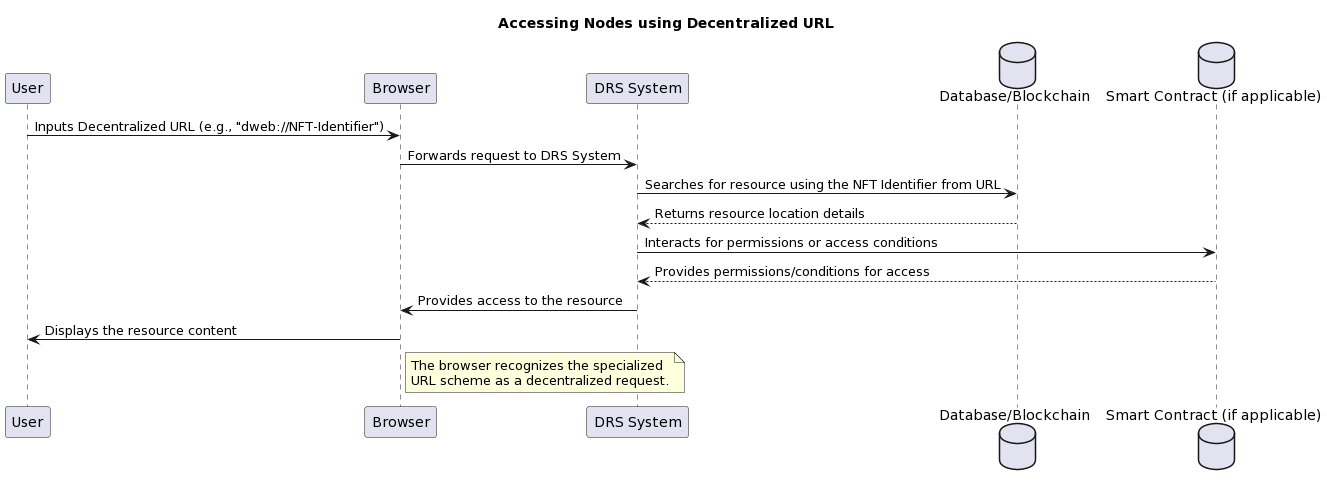
Diagram 36. Accessing nodes using a distributed URL
Accessing Nodes in a DRS System using a Distributed URL
A unique URL scheme distinguishes distributed resources from traditional web addresses, allowing the user to understand that they are accessing a distributed resource.
D. Label or Tag.
Labels or tags can be used similarly to short names, but can have arbitrary meanings unrelated to the content of the resource. They act as a descriptive layer on top of unique identifiers, increasing accessibility and understandability for users.
An example of such a query record may look like this
dweb://tags/research_paper/ipvx2023
Where:
dweb:// is an access pattern indicating that the resource is on a decentralised network.
tags is an indication that the following URL segment is a tag or tags.
research_paper is a specific tag that can describe a content type or topic. This helps users understand more quickly what a resource is about without even opening it.
ipvx2023 is a specific tag or identifier that can denote, for example, a document or research published in 2023 within the IPvX network.
Here is an example of how a tag-based system can function in a DRS (Distributed Resolver Service) environment [33]:
Accessing nodes in a DRS system using labels or tags: 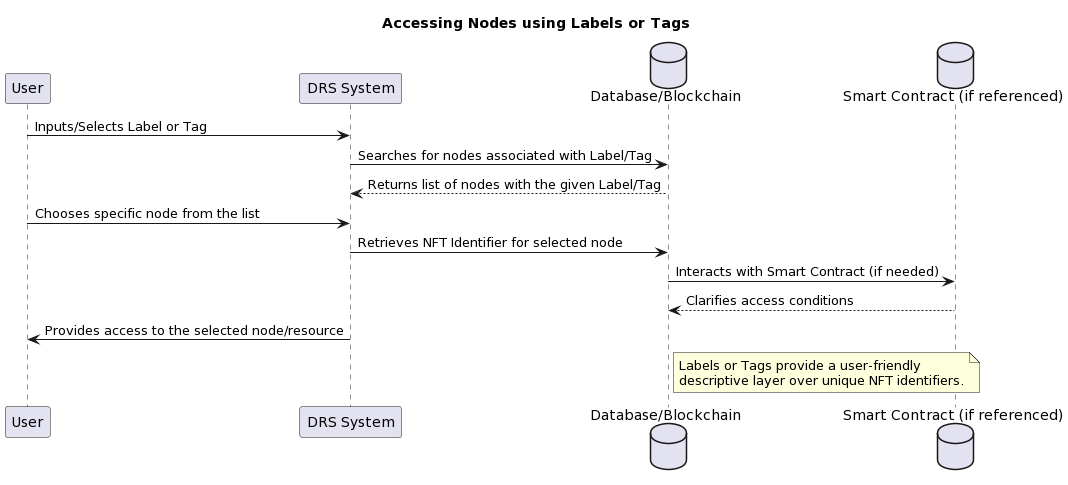
Diagram 37. Accessing nodes using labels and tags
This method allows users to navigate and search for resources in a more intuitive way, without the need for exact NMT identifiers.
E. Keyword Search.
If a browser or other system for generating a resource query has a search function, users can enter keywords for which the system will generate the corresponding NFT identifiers. This allows users to find resources even if they do not know the exact identifier [6].
An example of a search query is
Suppose a user wants to find a research paper on Internet decentralisation in the IPvX system. He does not know the exact identifier for this article, so he enters the following query into the browser or search interface:
“Research paper on Internet decentralisation in IPvX”.
The system responds with a list of relevant resources, each associated with a unique NFT identifier. For example:
dweb://tags/research_paper/decentralisation_ipvx2022
dweb://tags/article/ipvx_internet_transformation_2023
dweb://tags/report/decentralised_web_ipvx_review_2021
In this way, the user can access resources that match their request without having to know or enter exact identifiers.
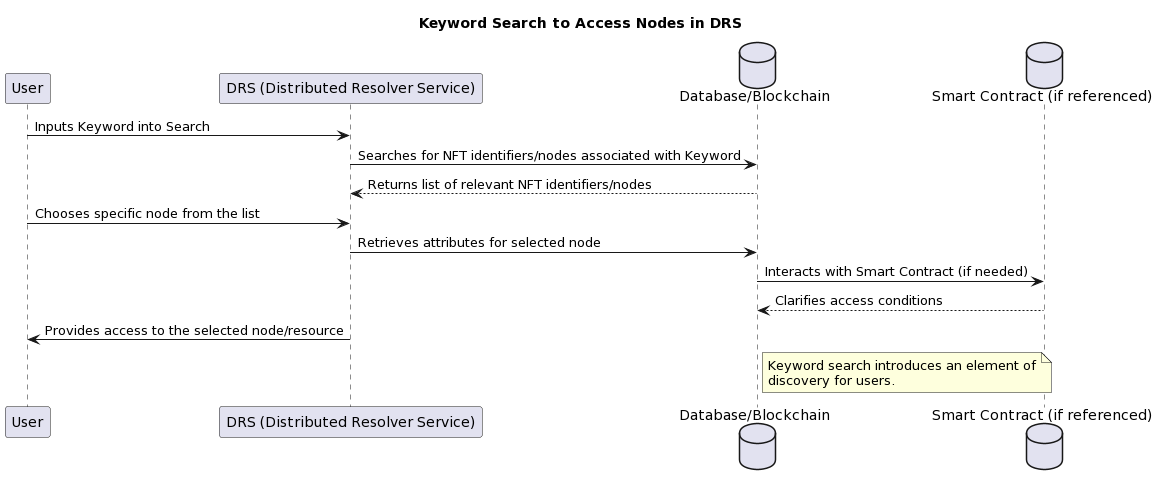
Diagram 38. Keyword search for accessing nodes in DRS
Keyword search for accessing nodes in DRS:
F. QR Code Scanning.
Scanning QR codes to search for resources on the network, which has already become common in the mobile environment, can also allow users to quickly access the searched nodes based on NFT identifiers. This solution provides a fast and convenient connection to the resources without the need for manual input [16].
In general, visually this solution does not differ from the existing practice of embedding links to the URL of the searched document or site in the QR code, only in the IPvX system we will use a direct link to the NFT identifier. 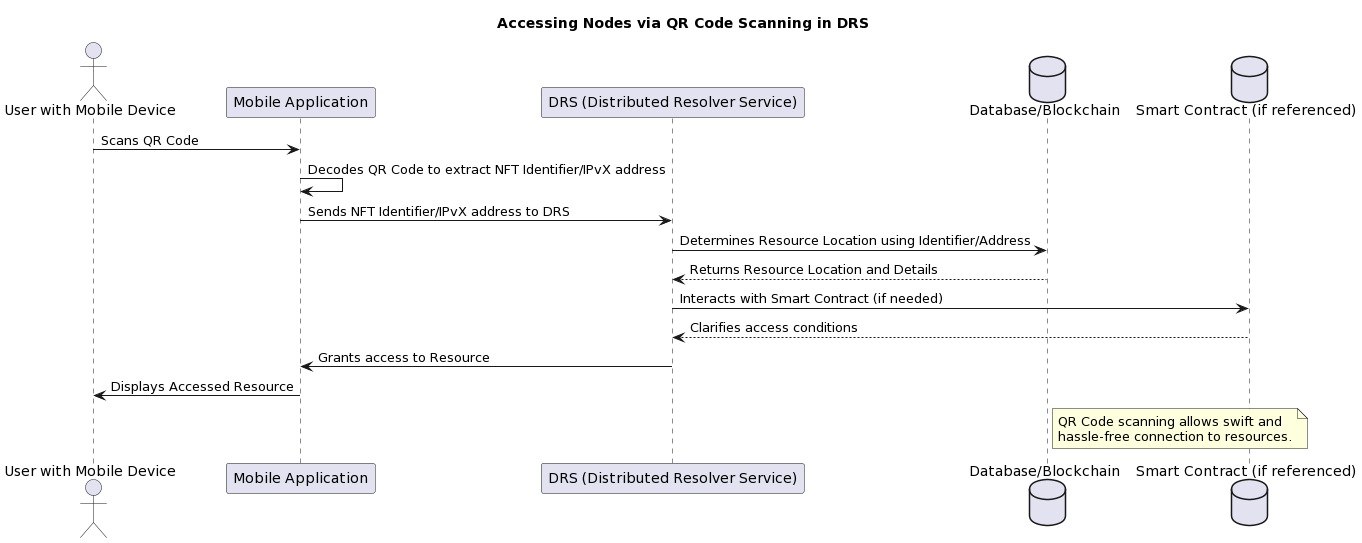
Diagram 39. Accessing Nodes by Scanning QR Codes in DRS
Accessing Nodes by Scanning QR Codes in DRS
The use of QR codes provides seamless, efficient and error-free user access to resources on the IPvX network without the need to manually enter complex NMT identifiers.
VIII. Conclusion.
Of course, in this short review we cannot cover all the technological aspects of the formation of a new IPvX ecosystem [5], for this it is necessary to invest a lot of time and effort, involving in the process public organisations and Internet experts [10], as well as key players in the IT market.
This article is a small extract of ideas and developments that our institute has carried out in recent years [10].
Transitioning to a new frontier of Internet infrastructure development is not an easy task, just remember how many years a banal protocol change from IPv4 [22] to IPv6 [25] takes, and it is far from over.
But it is already obvious that if we do not implement something fundamentally new for the Internet infrastructure in 20 years, we will have a landscape with an outdated architecture at that time, IPv6 [25] addressing, which does not meet the norms of the time, at least because its basic principles were laid down in the 1950s of the last century [1] and do not even correspond to the current challenges of the time, let alone the prospects for the next 10-20 years.
I am not even going to talk about the Domain Name System, it is obvious to everyone that it is a set of crutches that is trying to drag the Internet into the future, mainly due to the fault of the current Internet bureaucracy [3][18], which, as they say, is terribly far from ordinary users and their needs and requirements.
Therefore, the transition to a decentralised network architecture is an inevitable evolutionary process that must be initiated now [32][33][34].
Alexey Shkittin, August 2023, Berlin.
References.
[1] – Clark, D. (1988). The Design Philosophy of the DARPA Internet Protocols. ACM SIGCOMM Computer Communication Review, 18(4), 106-114 (https://dl.acm.org/doi/pdf/10.1145/52325.52336)
[2] – Mockapetris, P. (1987). Domain names – concepts and facilities. RFC 1034. ( https://datatracker.ietf.org/doc/html/rfc1034)
[3] – Albitz, P., & Liu, C. (2006). DNS and BIND (5th ed.). O’Reilly Media, Inc. http://www.nylxs.com/docs/dnsandbind_5thedition.pdf
[4] – Observed DNS Resolution Misbehavior” (Vixie, P., & Kato, A., 2006) available at RFC 4697. (https://www.rfc-editor.org/rfc/pdfrfc/rfc4697.txt.pdf)
[5] – [Davie, B., & Farinacci, D. (2011). Internet Protocol, Version 10 (IPv10): Another Next Generation IP. Internet Draft].
https://datatracker.ietf.org/doc/pdf/draft-omar-ipv10-10 )
[6] – Qin Wang, Rujia Li, Qi Wang, Shiping Chen, Non-Fungible Token (NFT): «Overview, Evaluation, Opportunities and Challenges. Retrieved»
[7] Antonopoulos, A. M., & Wood, G. (2018). Mastering Ethereum: Building Smart Contracts and Dapps. O’Reilly Media.
[8] Tapscott, D., & Tapscott, A. (2016). Blockchain revolution: How the technology behind bitcoin is changing money, business, and the world. Penguin. (https://books.google.de/books?id=NqBiCgAAQBAJ&printsec=frontcover&hl=ru#v=onepage&q&f=false)
[9] – Greenstein, S. (2015). How the Internet Became Commercial: Innovation, Privatization, and the Birth of a New Network. Princeton University Press.
[10] The “Private institute for the development of public digital networks” gGmbH (https://iedn.net/en/homepage/)
[11] – M. Nadini, L. Alessandretti, F. Di Giacinto, M. Martino,
L. M. Aiello, A. Baronchelli. (2021).
Mapping the NFT revolution: market trends, trade networks,
and visual features. (nature.com) (https://www.nature.com/articles/s41598-021-00053-8.pdf)
[12] – Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System. [Bitcoin Whitepaper](https://bitcoin.org/bitcoin.pdf)
[13] – Wattenhofer, R. (2016). The Science of the Blockchain. Inverted Forest Publishing.
[14] – Zohar, A. (2015). Bitcoin: Under the Hood. Communications of the ACM, 58(9). (https://dl.acm.org/doi/pdf/10.1145/2701411)
[15] – Hoffman, P. (2018). “RFC 9364 DNS Security Extensions (DNSSEC)”. (https://www.rfc-editor.org/rfc/rfc9364.pdf)
[16] – TANVEER ZAFAR • (2022 )Blockchain, NFTs and the New Standard for Identity and Security. Entrepreneur. (https://www.entrepreneur.com/money-finance/blockchain-nfts-and-the-new-standard-for-identity-and/403417)
[17] – J. Liu, B. Li, L. Chen, M. Hou, F. Xiang, and P. Wang, “A data storage
method based on blockchain for decentralization dns,” in IEEE DSC,
2018, pp. 189–196
[18] – Mockapetris, P. (1987). Domain Names – Implementation and Specification. RFC 1035. (https://datatracker.ietf.org/doc/html/rfc1035)
[19] – Vixie, P. et al. (1997). Dynamic Updates in the Domain Name System (DNS UPDATE). RFC 2136. (https://datatracker.ietf.org/doc/html/rfc2136)
[20] – Andrews, M. (1998). Negative Caching of DNS Queries (DNS NCACHE). RFC 2308. (https://datatracker.ietf.org/doc/html/rfc2308)
[21] – Arends, R. et al. (2005). DNS Security Introduction and Requirements. RFC 4033. (https://datatracker.ietf.org/doc/html/rfc4033)
[22] – Postel, J. (1981). Internet Protocol. RFC 791. (https://datatracker.ietf.org/doc/html/rfc791)
[23] – Postel, J. (1981). Internet Control Message Protocol. RFC 792. (https://datatracker.ietf.org/doc/html/rfc792)
[24] – Baker, F. (1995). Requirements for IP Version 4 Routers. RFC 1812. (https://datatracker.ietf.org/doc/html/rfc1812)
[25] – Deering, S., Hinden, R. (1998). Internet Protocol, Version 6 (IPv6) Specification. RFC 2460. (https://datatracker.ietf.org/doc/html/rfc2460)
[26] – Hinden, R., Deering, S. (2006). IP Version 6 Addressing Architecture. RFC 4291. (https://datatracker.ietf.org/doc/html/rfc4291)
[27] – Narten, T. et al. (2007). Neighbor Discovery for IP version 6 (IPv6). RFC 4861. (https://datatracker.ietf.org/doc/html/rfc4861)
[28] – Rekhter, Y., Li, T., Hares, S. (2006). A Border Gateway Protocol 4 (BGP-4). RFC 4271. (https://datatracker.ietf.org/doc/html/rfc4271)
[29] – Bates, T., Chen, E., Rekhter, Y. (2006). BGP Route Reflection: An Alternative to Full Mesh Internal BGP (IBGP). RFC 4456. (https://datatracker.ietf.org/doc/html/rfc4456)
[30] – Bates, T. et al. (2007). Multiprotocol Extensions for BGP-4. RFC 4760. (https://datatracker.ietf.org/doc/html/rfc4760)
[31] – Ethereum Network Status. [(accessed on 3 August 2020)]; Available online: https://ethstats.net.
[32] – Namecoin,” https://namecoin.org/.
[33] S. Gourley an d H. Tewari, “Blockchain backed dnssec,” in International
Conference on Business Information Systems. Springer, 2018. (https://www.researchgate.net/publication/326489781_Blockchain_Backed_DNSSEC)
[34] A. d. L. R. Gomez-Arevalillo and P. Papadimitratos, “Blockchain-based public key infrastructure for inter-domain secure routing,” in IFIP INET-
SEC, 2017. (https://people.kth.se/~papadim/publications/fulltext/SBTM-blockchain-secure-routing.pdf)
[35] Q. Xing, B. Wang, and X. Wang, “Bgpcoin: Blockchain-based internet
number resource authority and bgp security solution,” Symmetry, vol. 10,
no. 9, p. 408, 2018.(https://www.mdpi.com/2073-8994/10/9/408)
[ 36] – Hu N, Teng Y, Zhao Y, Yin S and Zhao Y. (2021). IDV: Internet Domain Name Verification Based on Blockchain. Computer Modeling in Engineering & Sciences. 10.32604/cmes.2021.016839. 129:1. (299-322).
(https://www.techscience.com/CMES/v129n1/44202)
[37] – Lu G, Jia X, Zhang Y, Shao J and Wei G. (2023). A domain name management system based on account-based consortium blockchain. Peer-to-Peer Networking and Applications. 10.1007/s12083-023-01455-3. 16:2. (1211-1226). Online publication date: 1-Mar-2023.
(https://link.springer.com/10.1007/s12083-023-01455-3Lu G)